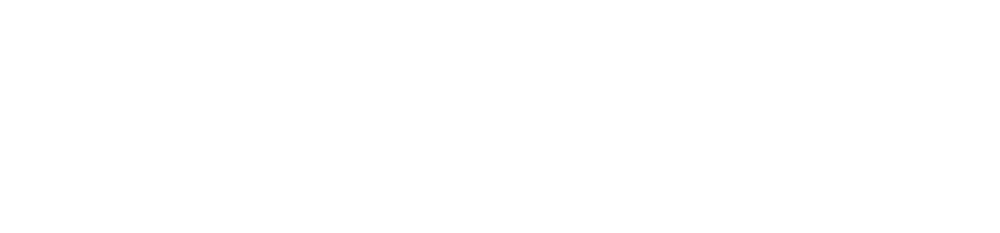Singlesig vs Multisig: What's Best For Crypto Cold Storage?
In this guide, we'll explore the differences between singlesig (single signature) and multisig (multi signature) wallets, understanding why the latter is the preferred choice for those managing sizable balances.
If you're looking for the best ways to secure digital bearer assets like Bitcoin and other cryptocurrencies, it's important to undestand the differences and pros & cons, between singlesig and multisig: the two predominant wallet structures in the world of cryptocurrency cold storage.
With the surge in Bitcoin's popularity and, naturally, its value, the importance of self-custody cannot be overstated. Some advocate treating your $10k worth of Bitcoin as if it were $100k, and $100k as if it were $1 million. This mindset stems from the potential rapid appreciation of Bitcoin holdings, which can occur over mere months or years. Without a meticulously planned security model, you may encounter significant challenges.
This guide provides invaluable insights for determining whether a singlesig or a multisig solution is preferable for your circumstances. Your choice can profoundly impact the security and accessibility of your funds. But with the right knowledge, you can make a well-informed decision that resonates with your requirements and level of comfort. Let's dive in.
Singlesig and Multisig: Main Differences
Transitioning your cryptocurrency holdings from exchanges (custodial platforms like Kraken or Coinbase) to non-custodial hardware wallets, which serve as cold storage solutions like the Blockstream Jade, Trezor, or Coldcard, marks a critical step in mitigating significant risks. This precautionary measure is pivotal considering the historical instances where exchanges have faced bankruptcy or experienced massive breaches, resulting in the loss or theft of users' funds.
Once you've resolved to assume self-custody of your Bitcoin/altcoins, the next question is about the methodology. While there exists a plethora of hardware wallets to choose from, the decision extends beyond mere selection of the device to encompass the wallet structure itself.
This involves deliberation over options such as singlesig, multisig, and other methodologies dictating the requisite number of private key signatures necessary for executing Bitcoin transactions.
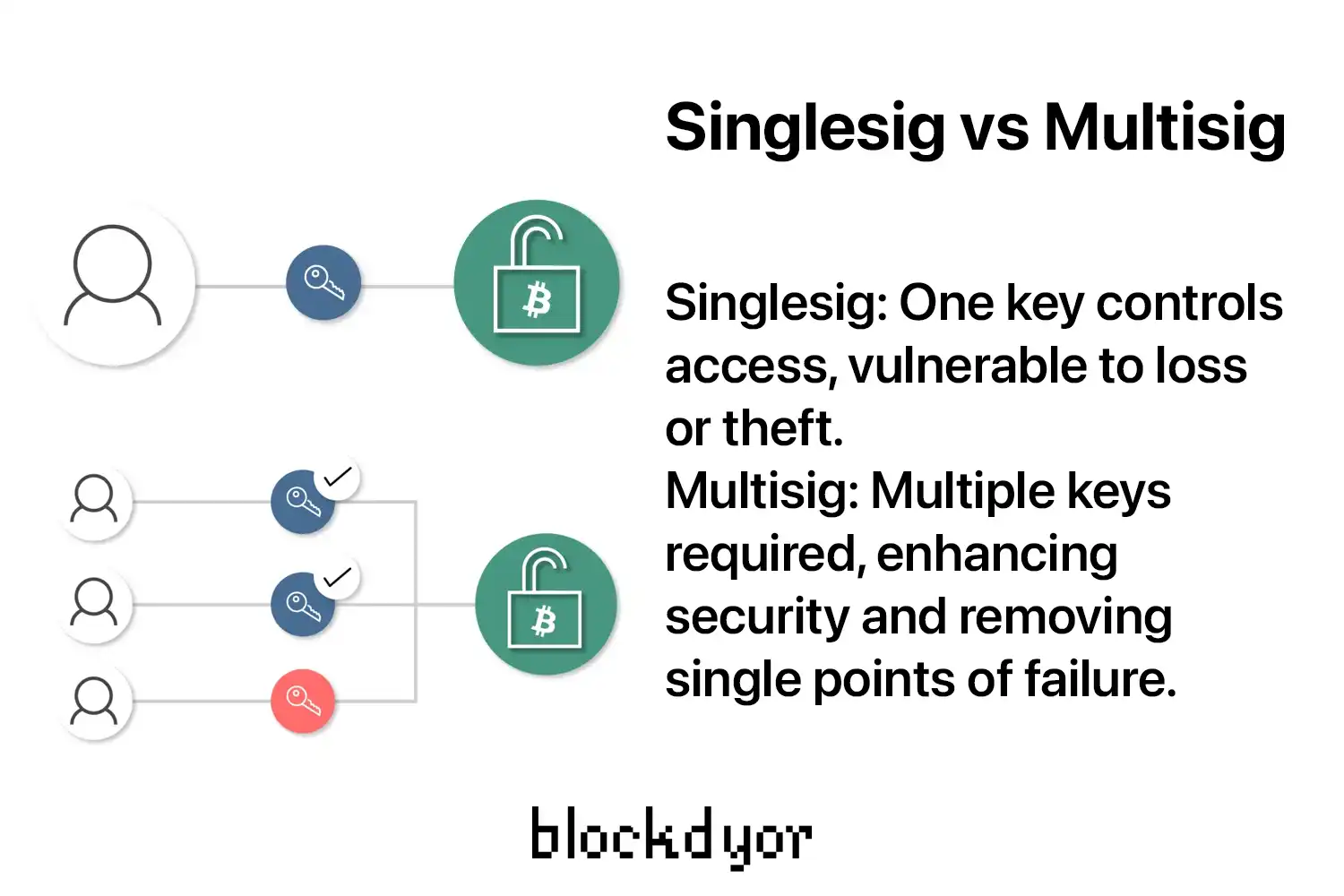
Singlesig (Single Signature)
Singlesig (Single Signature) stands as the prevailing choice among users, representing a wallet structure where a single private key suffices to authorize outgoing Bitcoin transactions. It's the most widespread method, with statistics indicating that over 70% of the total Bitcoin supply currently adheres to this format, constituting the oldest approach to "hodling" Bitcoin.
While singlesig offers relative ease of setup and a seemingly stress-free solution, particularly when the seed phrase has sufficient entropy and is generated in an airgapped manner, critics—primarily from the technical realm—assert that this approach lacks adequate security measures.
Indeed, singlesig introduces a single point of failure, thereby risking complete loss of funds. For instance, misplacement of recovery papers (the backups) coupled with hardware wallet malfunction or data loss results in irretrievable loss of the private key and associated funds. Furthermore, unauthorized access to the wallet or, worse yet, the recovery key enables nefarious individuals to transfer funds to their own wallets, albeit such occurrences are infrequent but plausible.
Private keys for Bitcoin (or altcoins) can be generated randomly via a simple button press or by utilizing user-generated entropy, such as through dice rolls (supported by wallets like the Coldcard). These details can be generated offline using hardware wallets and can even be physically stored in the form of a mnemonic phrase, typically comprising 12 or 24 words arranged in a specific sequence, suitable for paper or, ideally, steel storage.
However, if organizational challenges impede the secure storage of even basic materials like paper or steel/titanium plates, other solutions may be necessary. Before going into the world of multisig, let's first explore some "tricks" employed in singlesig configurations.
| Singlesig | |
|---|---|
| ❌ Single Point of Failure | Yes |
| 😕 Easy To Lose | Yes |
| 🔒 Easy To Get Stolen | Yes |
| 👍 Usability | Easy |
| 💸 Transaction Fees | Low |
| 🔐 Privacy | High |
Singlesig Security "Tricks"
There are some ways to increase single signature "security" in a sense that diminish the risks of losing the funds, not really for increasing the security of the setup from external actors. Let's have a look at some of these solutions.
Seed Phrase Duplication
The simplest and most cost-effective approach involves duplicating the seedphrase on multiple backup papers or, for enhanced durability, on seed steel plates. Remember, paper is susceptible to color loss, burning, and water damage. By making copies of the seedphrase on additional papers or plates, you increase security against potential loss or destruction.
This strategy proves particularly useful if you have multiple residences or wish to distribute copies of the seedphrase within a single location. Should one copy be misplaced or damaged, having another readily accessible ensures recovery. However, this method also introduces a vulnerability: if a thief gains access to any location where a backup paper is stored, they could steal the funds. Thus, multiple points of failure emerge, increasing the weakness inherent in singlesig setups.
To mitigate this risk effectively, consider the following approach:
- Hardware wallet (secured with at least a PIN) containing the seedphrase and serving as a backup.
- One paper backup stored within the house or in a household safe.
- One titanium plate stored alongside the paper backup for added durability.
This setup diversifies points of failure while leveraging the indestructible nature of titanium plates. By housing the plate alongside the paper backup, you avoid multiplying single points of failure. Additionally, the hardware wallet, acting as a signer, also functions as a backup containing the private key.
Multiple Singlesig Wallets
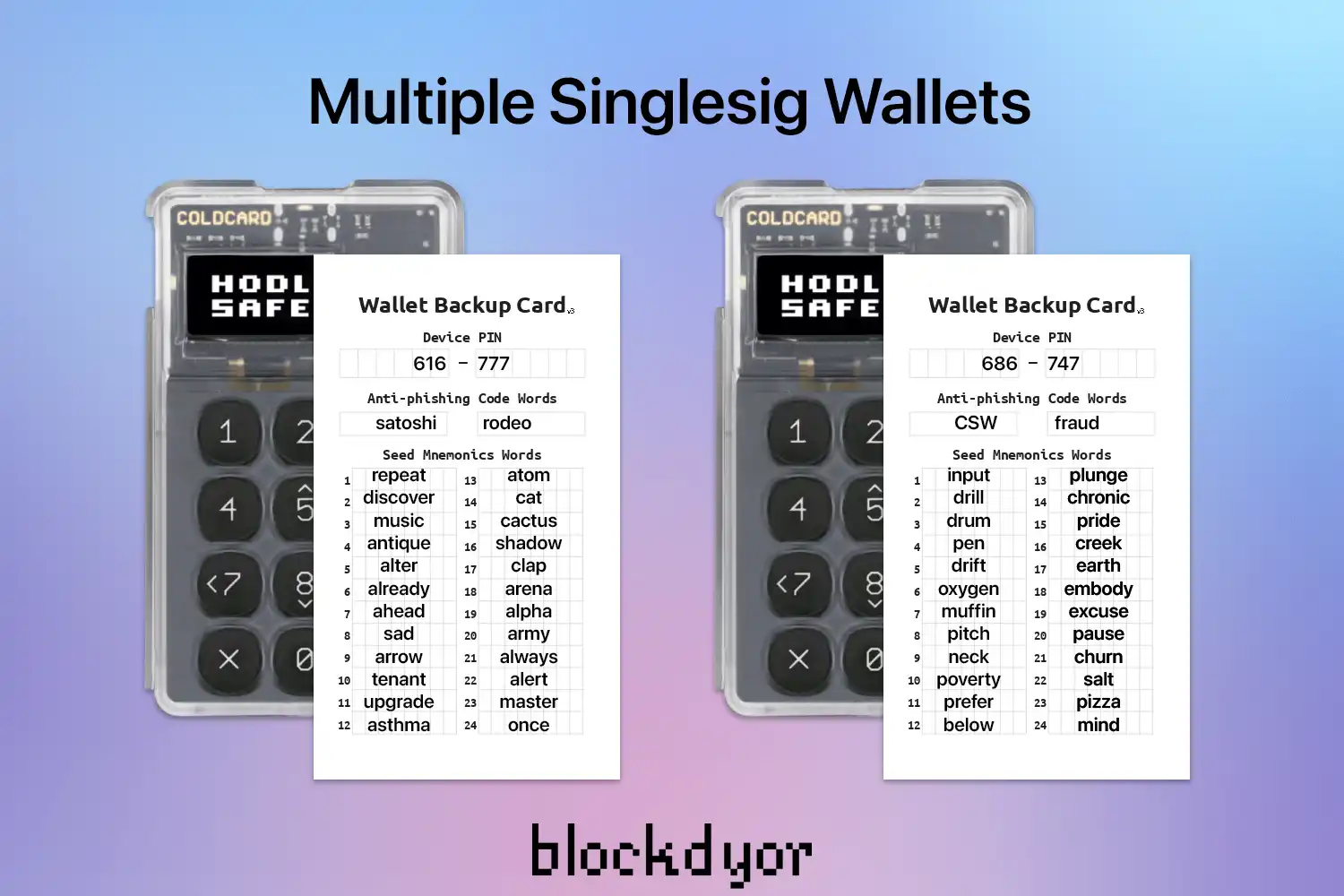
A commonly employed approach involves purchasing two or more hardware wallets from the preferred brand and distributing the funds across them in (more or less) equal proportions. This strategy mitigates the risk associated with all the balance in a single point of failure by diversifying it across multiple hardware devices.
However, there are drawbacks to this solution. It incur first of all in higher upfront costs, as well as needs the creation of additional paper backups and meticulous record-keeping. While it eliminates the risk of a single point of failure for the entire asset portfolio, it still introduces multiple smaller points of failure.
For instance, if you allocate your holdings evenly across two single-signature wallets like a Coldcard and a Blockstream Jade, and you lose one of the wallets + their backup, you would only lose "just" 50% of the funds. However, if both wallets were stolen together, the security measure would become ineffective as they could be stolen, lost, or damaged simultaneously.
Seed Phrase Splitting
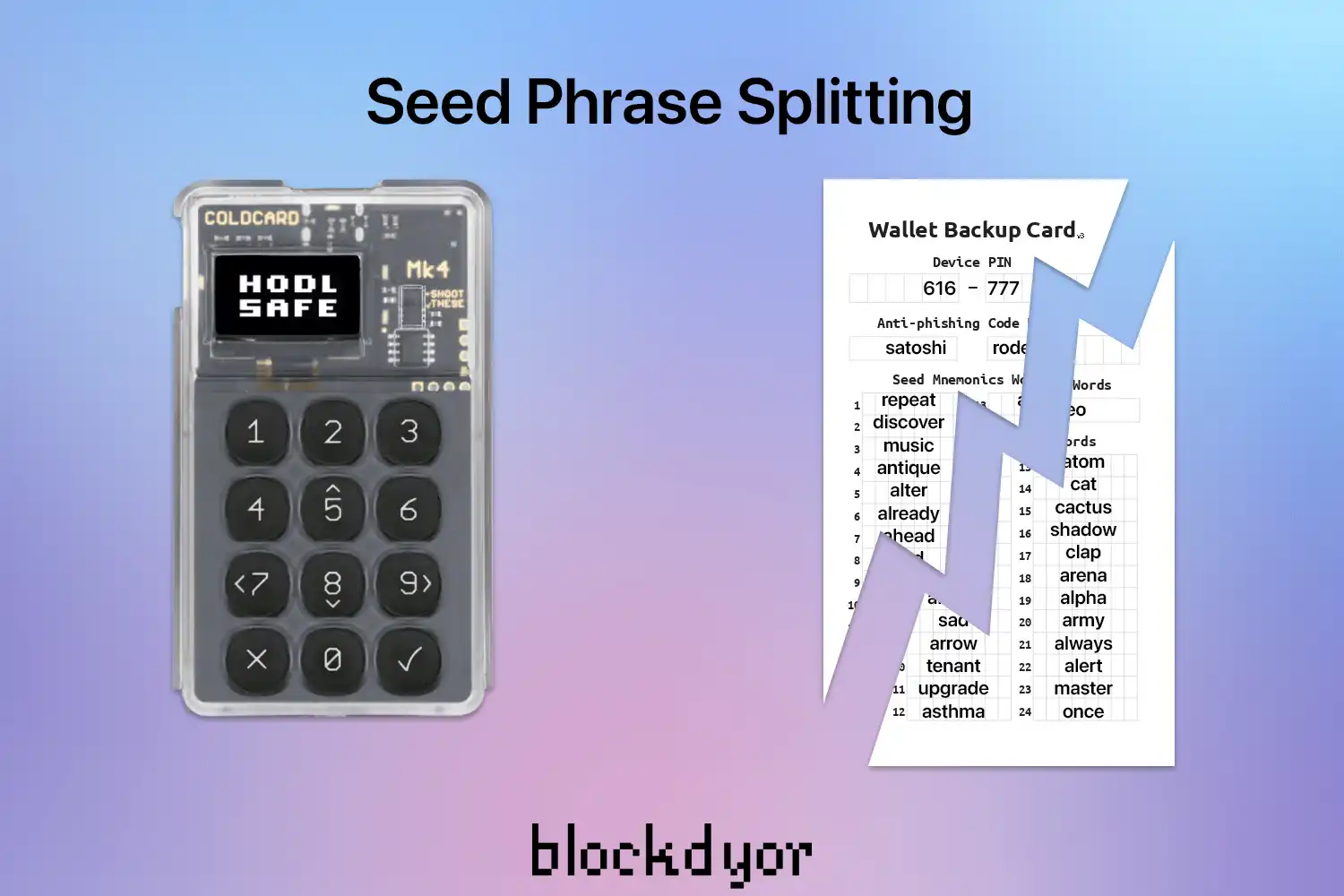
Another way some individuals may consider doing is splitting a single paper backup into two parts and storing them in separate locations. This method aligns with the typical length of seedphrases, which consist of either 12 or 24 words, allowing for a 50:50 split. However, while this may seem like a logical solution, it's not necessarily the safest one.
Splitting the backup into two parts, let’s say for a 24 words seedphrase by writing 12 words in one paper and the other 12 in another, introduces unnecessary complexity and risks. If one part is lost, burnt, or damaged, access to the funds is compromised. Furthermore, even with only one part in their possession, a thief may still have a (small) chance of retrieving the remaining portion of the seedphrase.
Basically, this solution serves as an over-complication rather than a solution to the problem. It not only makes basically impossible to access to your Bitcoin in the event of one part being lost but also potentially provides an opportunity for thieves to access your funds.
Seed Phrase Encoding
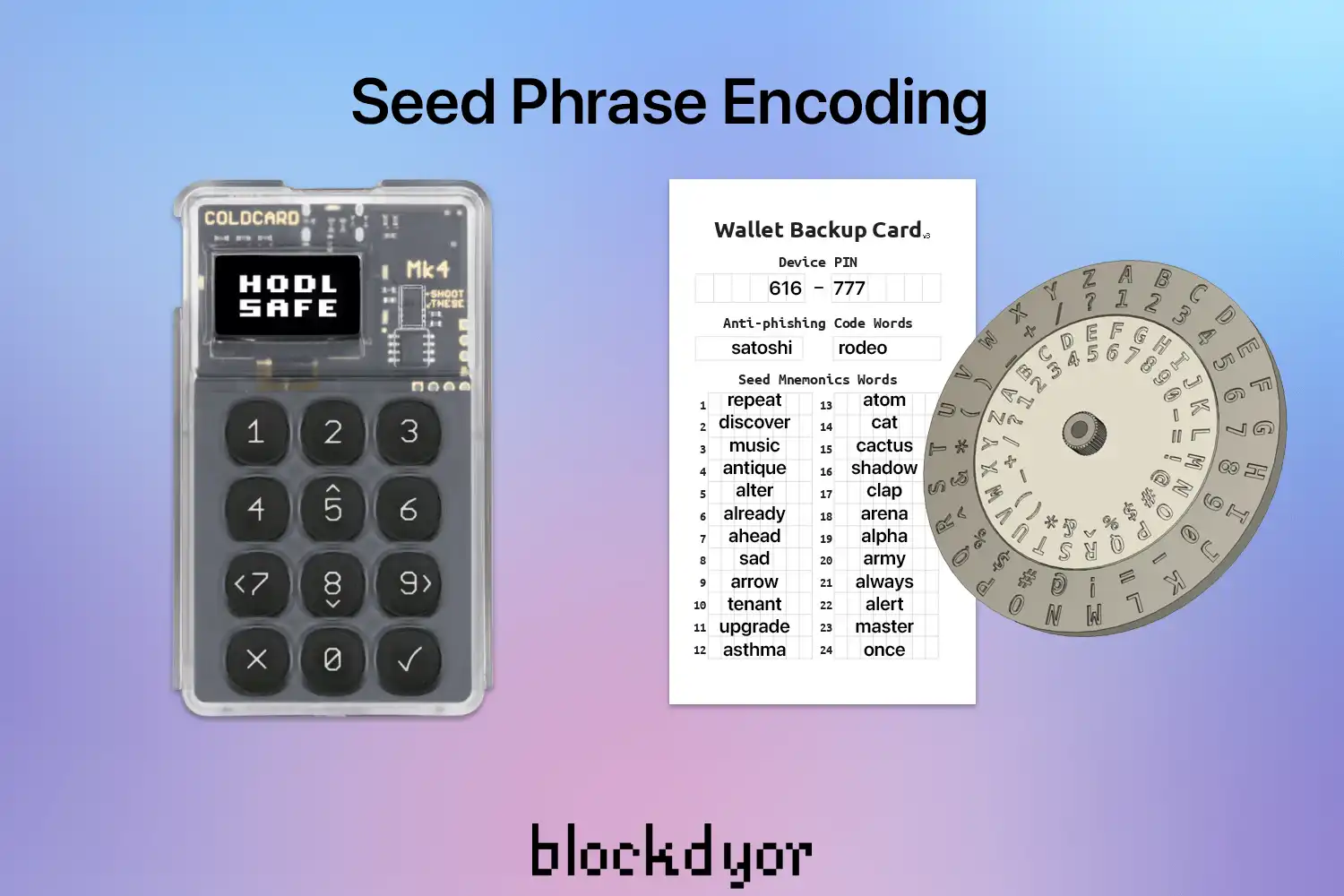
Another method frequently used to increase the security of a single signature wallet is to encode the seed phrase, often using techniques like the Caesar shift cipher. This cipher operates on a basic principle of substituting each letter in the plaintext with a letter found by moving a certain number of spaces down the alphabet. Originating from Julius Caesar's usage to conceal messages from adversaries, this cipher remains relevant even after two millennia.
This method serves to safeguard against potential theft scenarios wherein a thief gains access to the seed phrase but remains unable to decipher it to access the Bitcoin funds. The complexity of the encoding directly correlates with the difficulty for a thief to reverse engineer access to the funds.
However, using a complex encoding strategy has a double-edged sword. While it increases security, it also increases the likelihood of human error, potentially leading to the irreversible loss of access to funds.
Stateless Wallet

Stateless Wallets are devices designed to enhance security by erasing all sensitive information, such as private keys, when powered off. Each time the device is powered on, users must scan a recovery backup paper, which consists of a QR code instead of a traditional set of words.
This innovative approach eliminates the hardware wallet as a potential point of failure, significantly increasing security. The use of QR codes for recovery backup adds an additional layer of complexity, making it challenging for malicious actors to decipher or exploit.
It's important to note that if a skilled thief obtains the SeedQR, there's a significant risk of losing funds because the paper backup containing the QR code remains a single point of failure.
For further insights into this standard, refer to our comprehensive documentation on SeedQR.

Standard Singlesig Enhancements
In addition to the solutions outlined earlier, which essentially entail DIY attempts to bolster self-custody using these wallets, there are also some more technical solutions that are considered standards for implementation with hardware wallets.
These solutions include BIP39 passphrases, Shamir Secret Sharing, and Seed XOR. Widely used for their effectiveness, these methods address the vulnerabilities associated with single points of failure in a more sophisticated manner. Let's delve into how they function.
BIP39 Passphrase

The BIP39 Passphrase stands as a standard feature integrated into all hardware wallets, ranging from popular options like Ledger Nano S Plus to advanced models like the Coldcard. Essentially, when generating a wallet and its corresponding 12/24 words, you have the option to add a passphrase on top of it, thereby creating an entirely new wallet. This allows for the generation of personal entropy (randomness), giving the freedom to select any passphrase without being restricted to the predefined list of words from the BIP39 standards.
With the BIP39 passphrase, you can effectively establish a decoy wallet with a nominal balance, transferring the majority of funds to the wallet associated with the passphrase. The decoy wallet devoid of the passphrase serves as a diversion, while the concealed wallet linked to the passphrase holds the bulk of the funds. This strategy serves to safeguard your funds against potential threats such as the infamous "$5 wrench attack" or other perilous scenarios where someone might attempt to steal your wallet or, worse yet, coerce you to relinquish your funds.
The BIP39 passphrase works as an additional component to the existing 12 or 24 words, effectively serving as the 13th or 25th word. This passphrase is case-sensitive and can even incorporate special characters. Introduced in 2013 by the creators of BIP39 (the architects of seedphrases for recovering a private key), if a private key is generated with a passphrase, the passphrase will always be required to regenerate the key and access the funds.
Similar to seedphrase splitting, the BIP39 passphrase necessitates the seedphrase for fund access, and the seedphrase can be stored separately, rendering the entire setup more resilient to theft and essentially transforming it into something like a 2-of-2 multisig setup.
It's worth noting that one drawback of passphrases is that for optimal effectiveness, they should be stored separately from the wallet. Otherwise, their purpose is compromised, making them susceptible to loss. If the passphrase is lost, the funds are irretrievable.
Similarly, if you attempt to commit it to memory and subsequently forget it, the same outcome ensues. While passphrases offer an excellent means of strengthening security and effectively creating a "proto-multisig" 2 out of 2 setup, it's imperative to comprehend the implications before implementation. Many individuals have lost funds due to mishandling passphrases, underscoring the importance of conducting thorough research beforehand.
| Singlesig with Passphrase | |
|---|---|
| ❌ Single Point of Failure | Yes |
| 😕 Easy To Lose | Yes |
| 🔒 Easy To Get Stolen | No |
| 👍 Usability | Intermediate |
| 💸 Transaction Fees | Low |
| 🔐 Privacy | High |
Shamir's Secret Sharing

A method widely employed by hardware wallet manufacturers, particularly Trezor, is Shamir's Secret Sharing (SSS). This algorithm, devised in the 1970s, takes the private key and generates multiple pieces of information known as "shards" or shares (k out of n shares can reconstruct the secret). These shares are individually meaningless and require combination to reproduce the original secret.
Unlike multi-sig, SSS is blockchain-agnostic, offering a significant advantage for wallets supporting both Bitcoin and altcoins. Similar to multisig, SSS can be configured so that only a subset of the shards is necessary to retrieve the secret, rather than all of them.
SSS stands out as one of the most secure enhancements to traditional "singlesig" setups. It provides theft resistance without escalating single points of failure. For instance, in a 2 out of 3 SSS setup, if a thief steals one of the three shards, the funds can still be recovered, preventing the thief from accessing them. Additionally, if one of the shares is lost or damaged, the wallet owner can still access the funds. An attacker possessing up to k-1 shares cannot discern any information about the original secret.
By requiring only a portion of the shares to produce the secret, SSS boasts fewer points of failure compared to Seed XOR.
Regarding the integration of SSS in hardware wallets like Trezor, Satoshi Labs introduced SSS with the creation of the BIP39 standard, under a compatible standard called SLIP39. When setting up a Trezor Safe, users have the option to utilize SSS. Upon selection, the device generates the desired quorum of shards, each expressed as 20 words. Unlike Seed XOR or BIP39 passphrase, these shards cannot be used as a seed phrase for a "fake" or decoy wallet. Additionally, users must employ the SLIP39 special set of words, distinct from BIP39.
However, SSS also has its drawbacks. The primary concern is that during fund spending, the complete key must be retrieved by assembling the required shards, potentially exposing a window for exploitation. As the private key exists on a single device during splitting and is later reconstructed onto a single device for transaction signing, compromising the device at either stage could result in theft of the user's funds.
| Singlesig with SSS | |
|---|---|
| ❌ Single Point of Failure | Yes |
| 😕 Easy To Lose | No |
| 🔒 Easy To Get Stolen | No |
| 👍 Usability | Difficult |
| 💸 Transaction Fees | Low |
| 🔐 Privacy | High |
To learn more about Shamir Backup, follow the link down below to read the full review of the Cypherock X1, a SSS-only hardware wallet.
Seed XOR
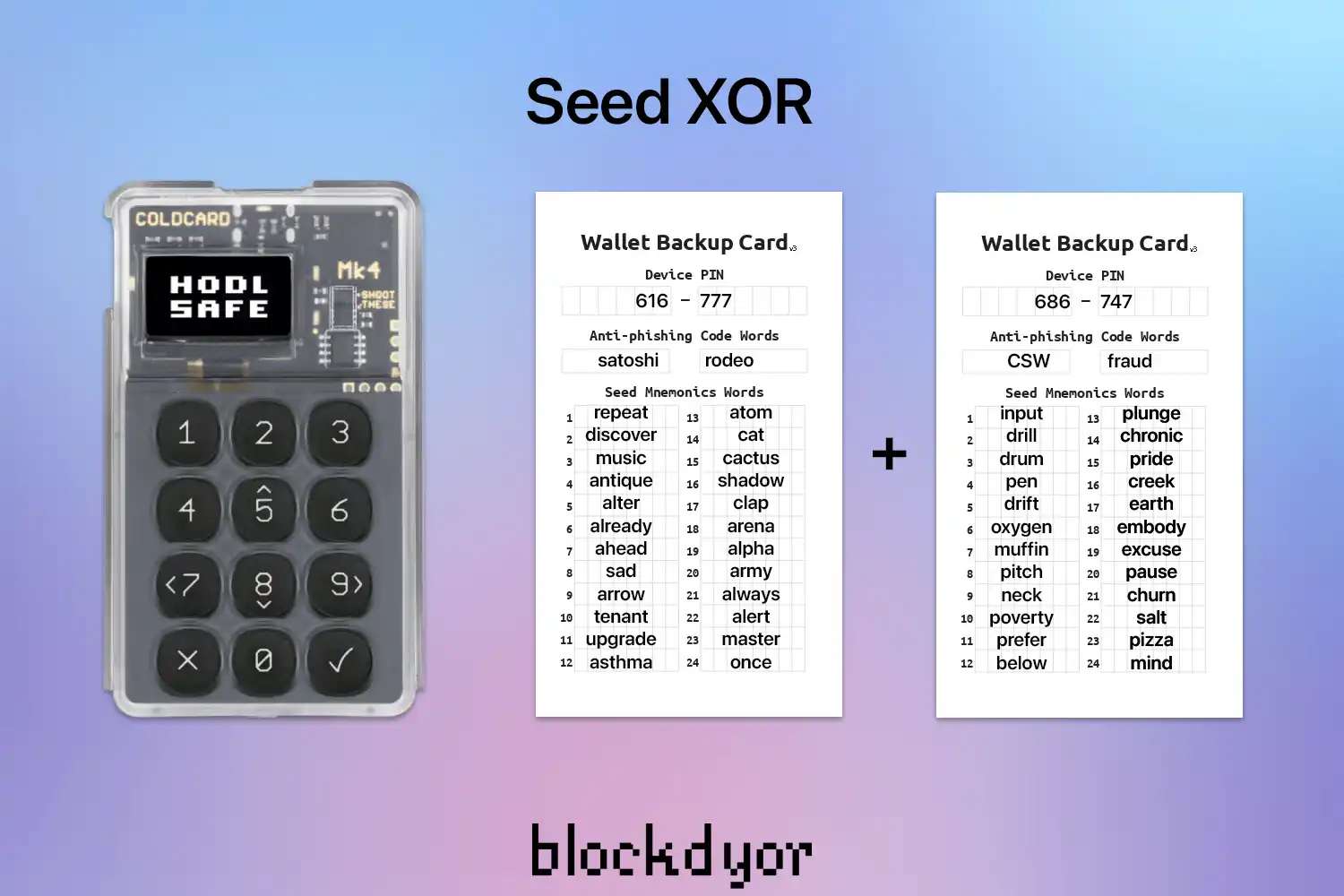
Coinkite, the company renowned for the Coldcard wallet series, has introduced an innovative security enhancement known as Seed XOR. This feature essentially enables the "splitting" of a seedphrase into two or more shards, each comprising 12 or 24 words, forming multiple seed phrases. To access the funds, one must reconstruct the original seed phrase by combining all the shards.
Unlike the DIY setups discussed earlier, Seed XOR offers a distinct approach to seed phrase splitting, devoid of the inherent vulnerabilities associated with multiple points of failure. Moreover, this setup also creates a decoy wallet, as each individual 12 or 24-word shard seedphrase can serve as a key for a new singlesig wallet.
Seed XOR represents a significant advancement in security, currently exclusive to Coinkite's devices. However, the computations necessary to split the seedphrase into two or more other seedphrases can also be performed manually, without reliance on the Coldcard (although thorough understanding of the process is essential).
Nevertheless, akin to previous "homemade" solutions such as passphrases or seed splitting, Seed XOR introduces its own set of challenges. While it effectively mitigates the risk of losing access to funds in the event of theft of one or more parts of the Seed XOR, it simultaneously increases the likelihood of losing access altogether. If one of the Seed XOR parts is lost, the ability to reconstruct the original key and access the funds within the wallet is compromised.
| Singlesig with Seed XOR | |
|---|---|
| ❌ Single Point of Failure | Yes |
| 😕 Easy To Lose | Yes |
| 🔒 Easy To Get Stolen | No |
| 👍 Usability | Difficult |
| 💸 Transaction Fees | Low |
| 🔐 Privacy | High |
Multisig (Multi Signature)
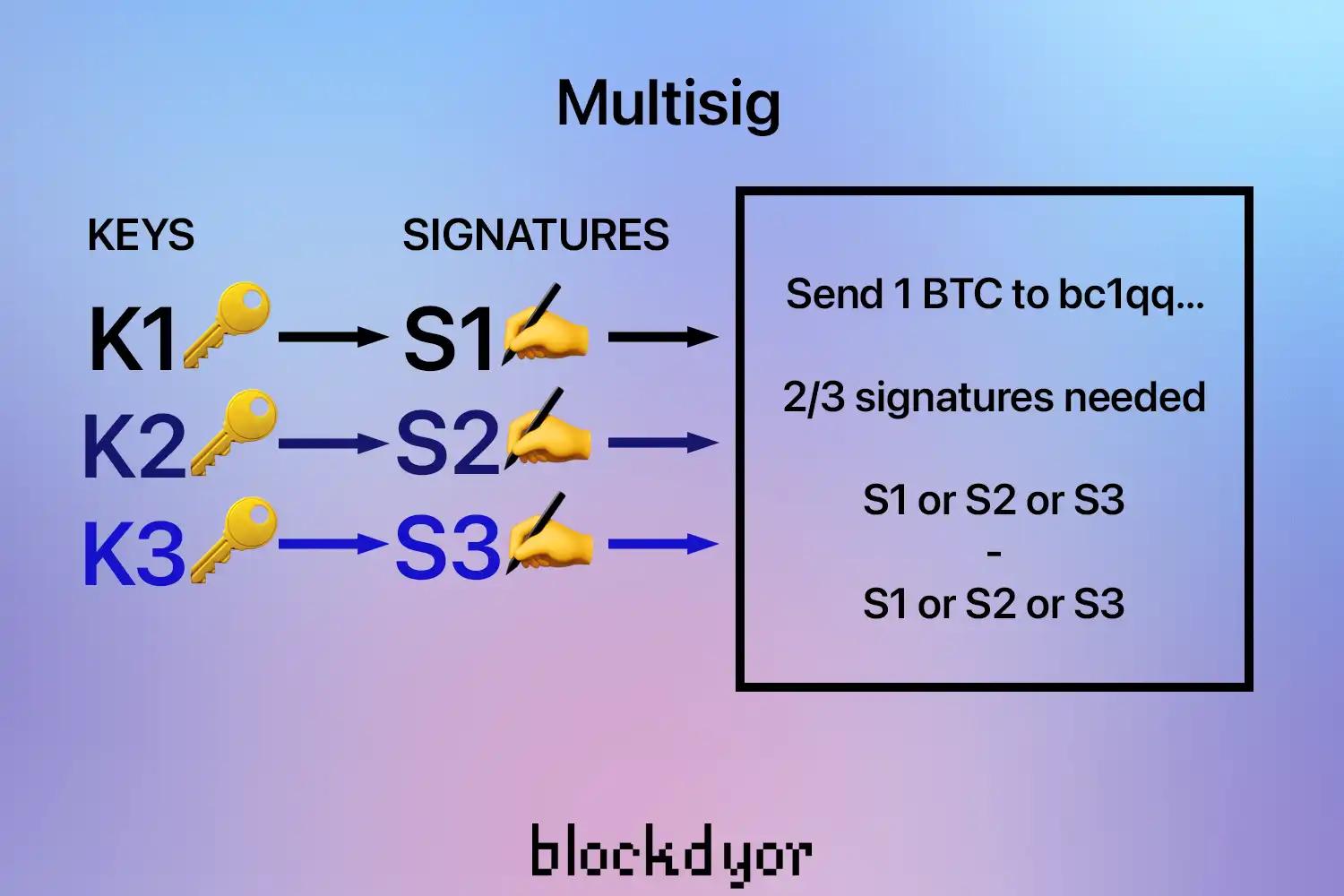
Multisig, short for multi-signature, represents a wallet structure obtained through multiple unique private keys. The number of keys utilized is determined by the creator of the wallet, along with the quorum required to spend the funds within it. The quorum denotes the minimum number of keys needed to authorize Bitcoin transactions and can range from 2 of 2 (requiring both keys for authorization) to 2 of 3, 2 of 4, and so forth.
The primary advantage of multisig lies in its elimination of single points of failure, thereby safeguarding Bitcoin from theft and loss. This feature renders multisig a preferred choice for securing significant Bitcoin trust and funds in cold storage. Furthermore, multisig is increasingly prevalent in both software and hardware wallets.
The 2 of 3 multisig setup is particularly common, striking a balance that facilitates collaborative custody arrangements. In such setups, one individual holds two keys while a collaborative custody partner holds one.
While the concept of quorum in multisig shares similarities with Shamir's Secret Sharing, multisig boasts a significant advantage: each key can independently sign transactions, irrespective of time or location. Unlike Shamir's Secret Sharing, where all shares are required simultaneously, multisig enables the signing of transactions with keys located separately.
Multisig offers a dynamic solution for managing Bitcoin treasuries or funds with multiple partners holding different keys.
| Multisig (DIY) | |
|---|---|
| ❌ Single Point of Failure | No |
| 😕 Easy To Lose | No |
| 🔒 Easy To Get Stolen | No |
| 👍 Usability | Advanced |
| 💸 Transaction Fees | Low |
| 🔐 Privacy | High |
Multisig Disadvantages
Despite its enhanced security compared to Shamir's Secret Sharing, multisig sacrifices some convenience for the end user. Users must possess a thorough understanding of the process, as losing access to a majority of the keys can result in funds becoming inaccessible.
In the past, transaction fees were higher for multisig transactions due to the higher number of signatures needed. However, with the Taproot update, signatures from all multisignature participants are recorded as one signature on the blockchain, resulting in the same fee structure as in singlesig transactions.
Unassisted Multisig vs Collaborative Custody Multisig
In multisig setups, a higher N-of-N ratio entails a greater risk of fund loss. While a lower quorum is more susceptible to theft, a higher quorum increases the risk of loss. Experts commonly regard 2 of 3 as the optimal setup.
However, the method of implementation—whether through unassisted multisig or collaborative custody—significantly impacts ease of use. Collaborative custody setups are generally more user-friendly than unassisted multisig, and inexperienced users are advised against attempting multisig setups independently.
Nevertheless, advancements in technology are making multisig setups increasingly accessible and practical for everyday users.
Collaborative Custody Solutions
When considering Collaborative Custody, it's essential to recognize that involving a collaborative custody partner, most of the times, entails additional costs, adding another drawback to multisig compared to singlesig.
Collaborative assisted custody typically entails a 2 out of 3 multisig setup, where you retain two keys and the third is held by the custodian. However, there are alternatives with higher quorums or even free services without a 3rd party custodian, offering a robust 2 out of 3 multisig setup in a do-it-yourself manner. Let's explore some of the most popular solutions.
| Multisig (Collaborative) | |
|---|---|
| ❌ Single Point of Failure | No |
| 😕 Easy To Lose | No |
| 🔒 Easy To Get Stolen | No |
| 👍 Usability | Easy |
| 💸 Transaction Fees | Low |
| 🔐 Privacy | Medium |
Nunchuck
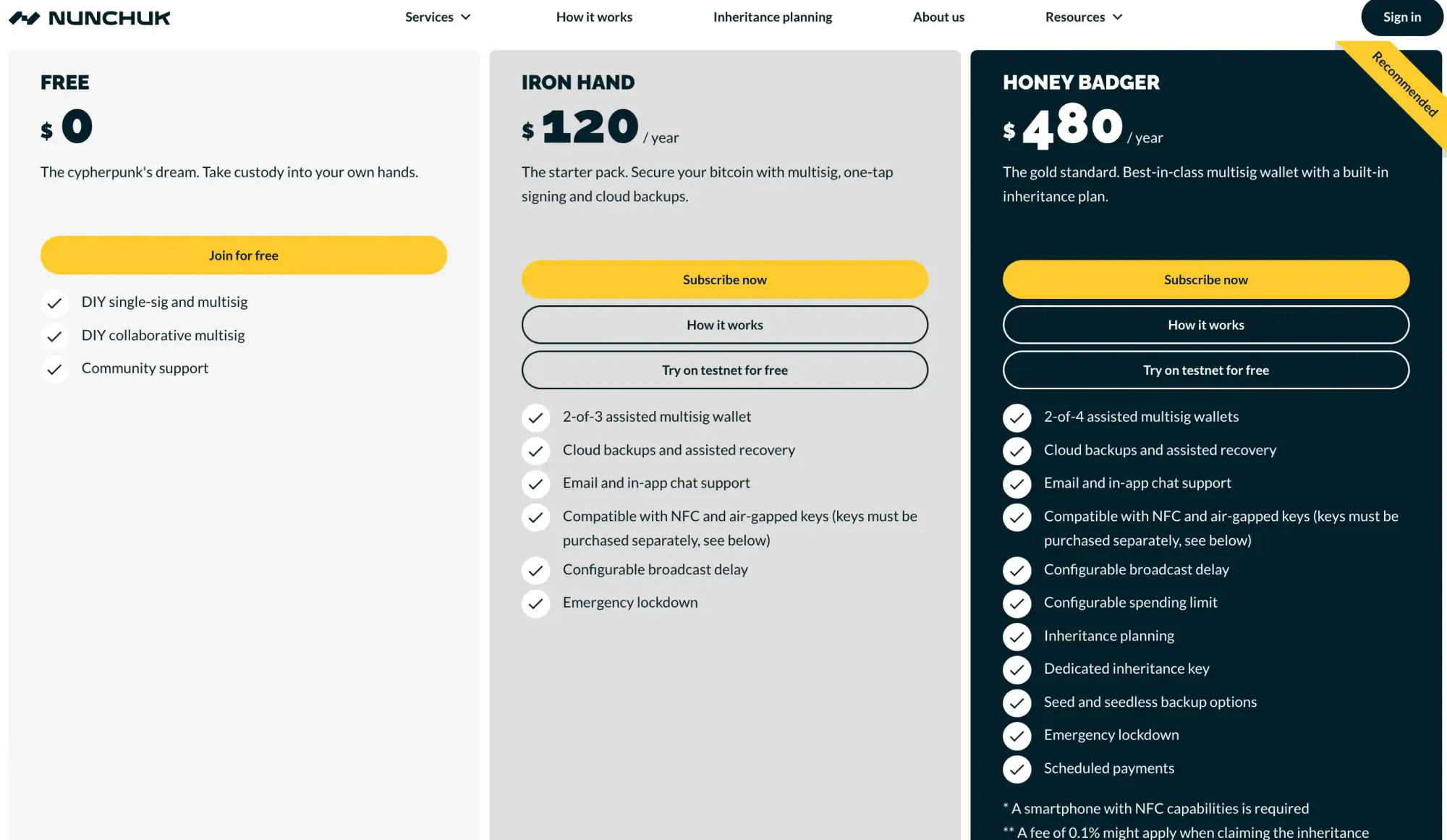
Nunchuck is a Bitcoin-only multisig platform offered as software, allowing users to incorporate their own hardware wallets and devices such as the Tapsigner. It provides a free tier with options for DIY single-sig, multisig, and collaborative multisig, alongside paid plans featuring assisted collaborative custody and inheritance arrangements with a dedicated inheritance key. This key, separate from the other keys in your wallet, is designed for future use at a date of your choosing.
It's likely the optimal choice for multisig and collaborative multisig setups, given its KYC-free nature, provision of a free tier, and compatibility with a wide range of hardware wallets. The platform offers desktop and Android versions that are open source, along with an iOS version. It's particularly useful when paired with NFC devices like the Coldcard or Tapsigner, enabling them to function as shares within your multisig configuration.
Swan Vault
Swan, the esteemed Bitcoin-only and Buy-only exchange, has embarked on a new venture with a "collaborative custody" service utilizing Blockstream's hardware wallet, Jade.
In a manner akin to other collaborative custody solutions, users oversee their Bitcoin holdings through a 2-of-3 multisig setup. Clients securely possess two keys offline using two Jade devices, while Swan retains a third key for recovery assistance if necessary.
The Swan Vault service ensures clients maintain complete control over their bitcoin with the 2-of-3 multisig setup. Two Jade devices are securely held offline by the customer, while Swan holds the third key for potential recovery scenarios. Additionally, the service offers advanced custody features such as dependable key backup options, collaborative vault systems, and multi-party spending permissions.
For further insights into Swan's offerings and to avail of a complimentary entry bonus, refer to the comprehensive review below.
Casa
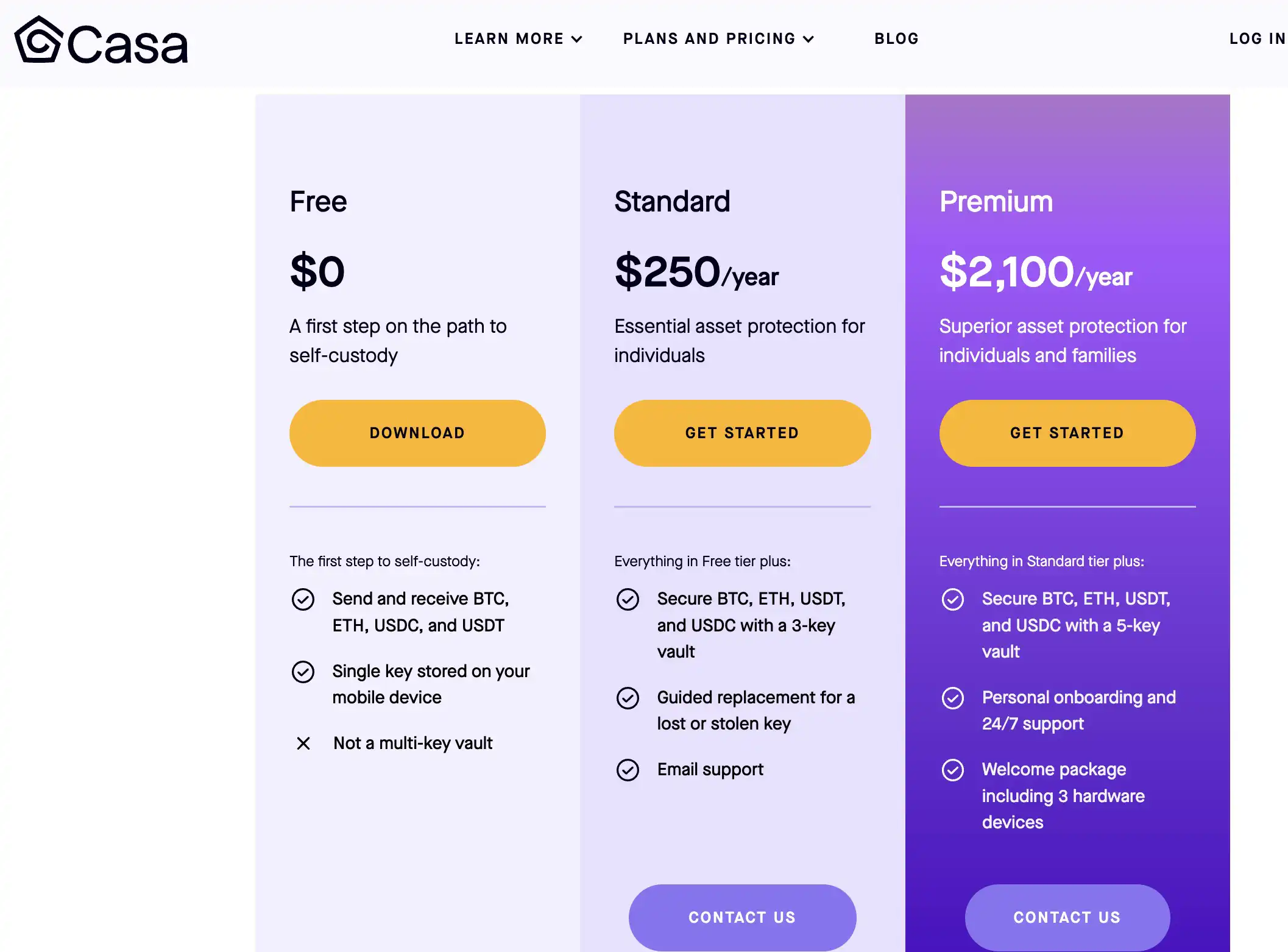
Founded by cypherpunk Jameson Lopp, Casa offers no free plans beyond a basic singlesig wallet. Their base multisig plan is pricier than Nunchuck's and follows the same 2-of-3 multisig structure.
However, Casa extends its services beyond Bitcoin, also supporting Ethereum, making it appealing for individuals, families, or companies seeking collaborative multisig setups encompassing both Bitcoin and altcoins.
Unchained
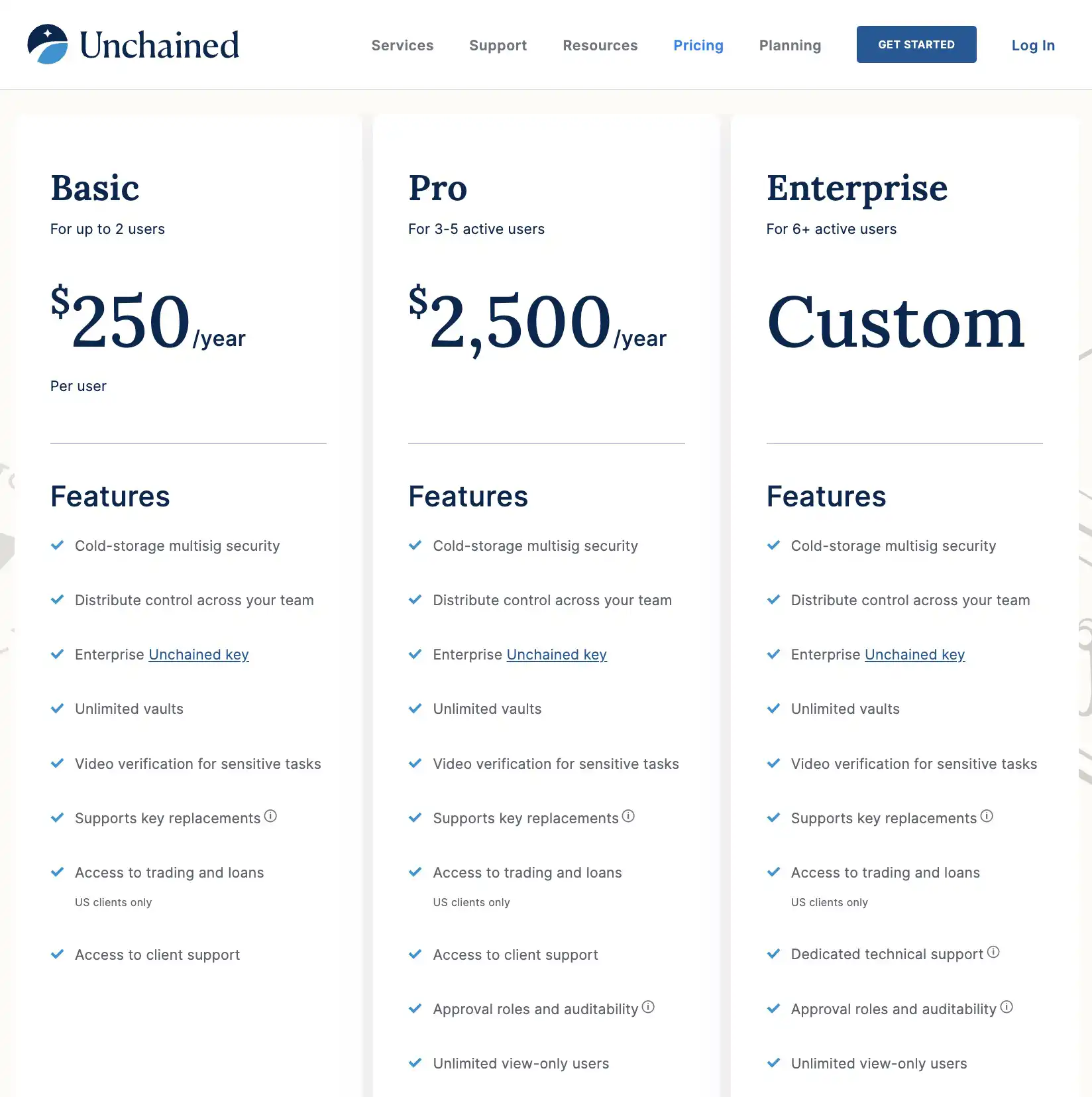
Unchained stands out as perhaps the most comprehensive and sophisticated solution for 2 out of 3 multisig setups. While lacking a free trial option, Unchained offers a multitude of setups and services, including trading, inheritance planning, loans, and IRAs. It's worth noting that these plans are available exclusively in the US.
Bitkey
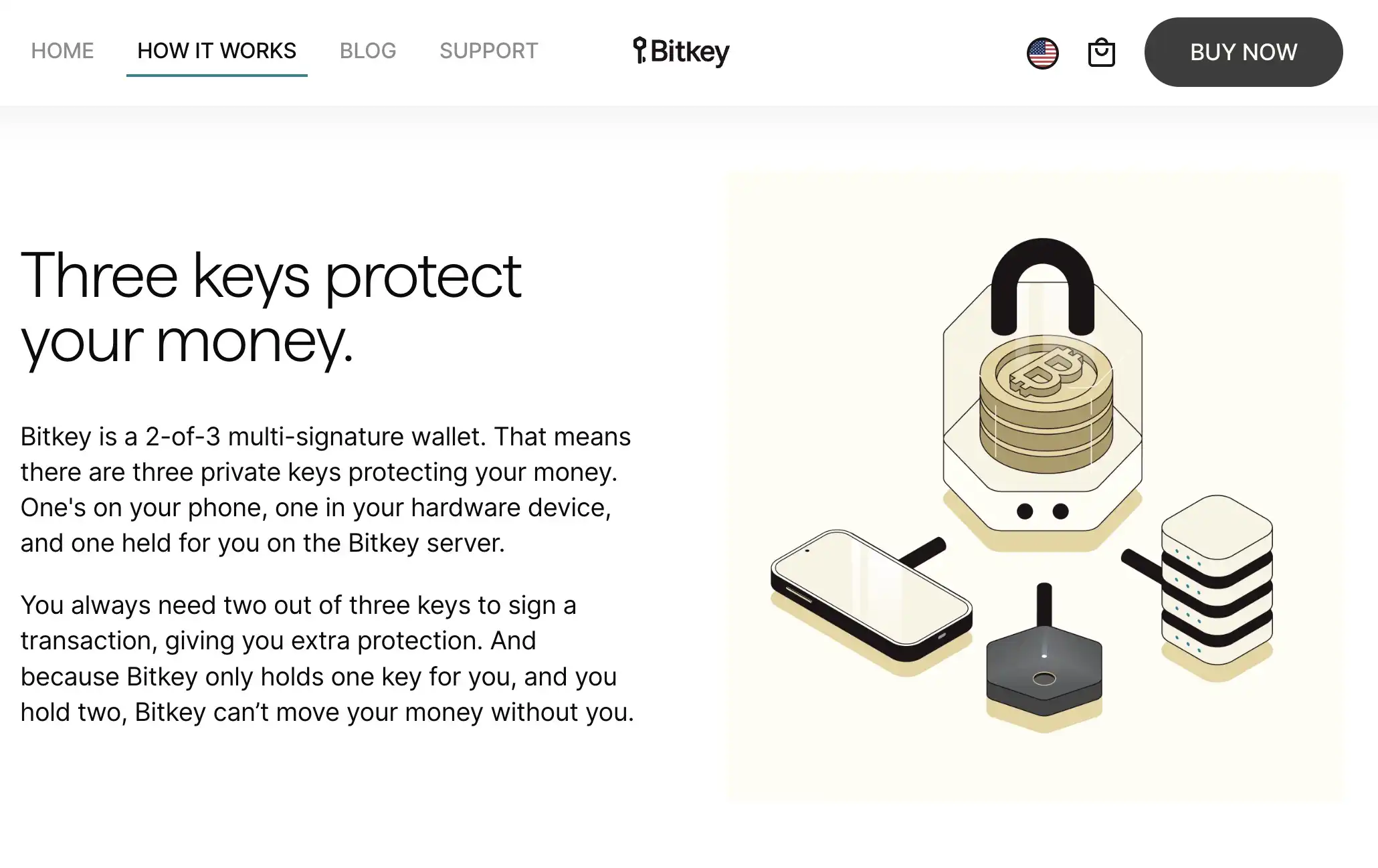
Bitkey, a 2-of-3 multi-signature hardware wallet affiliated with Jack Dorsey's enterprise, offers a distinctive approach to collaborative custody. One private key resides on your phone, another on your hardware device, and the third is held by Bitkey.
Transactions require the authorization of two out of three keys, enhancing security. With no subscription required for collaborative custody, users need only purchase the hardware wallet, priced around one hundred dollars.
Choosing between Singlesig and Multisig
When choosing between singlesig and multisig, it's crucial to consider various factors and the complexity each option entails. While multisig presents remarkable security benefits, it requires meticulous deployment and may not be suitable for non-technical users who aren't fully cognizant of its intricacies.
Multisig Considerations
Multisig, particularly in the realm of Bitcoin's on-chain transactions, is indeed a potent security tool with manifold applications. It offers robust protection against theft by eliminating single points of failure. However, its effectiveness hinges on proper deployment and user expertise.
Multisig addresses, generated from the public keys of participating parties, necessitate meticulous backup strategies. In scenarios like multi-actor multisig or single-user multisig, where multiple seeds are utilized, advanced technical proficiency is indispensable.
Similarly, in multi-user multisig setups, where additional service providers safeguard backups, expert supervision is essential.
Challenges with Multisig
Despite its efficacy, multisig poses challenges, particularly regarding recoverability. The nuances of managing multisig setups, understanding the mechanics of address generation, and ensuring comprehensive backup strategies can be daunting for inexperienced users. Attempting multisig without adequate knowledge and supervision may lead to irretrievable fund loss.
Singlesig as an Alternative
In contrast, singlesig offers simplicity and convenience, making it accessible to a broader user base. However, it inherently carries single points of failure, such as reliance on a single private key. While it's relatively straightforward to set up, singlesig may not provide the same level of security as multisig, especially for sizable holdings.
Indeed, in a 2 out of 3 multisig setup, losing one key doesn't result in any loss of funds since you still have two remaining keys. Whether the third key is under your control, your family's, business partner, or a custodian's, your funds remain accessible.
However, with singlesig, there's no room for error—losing even a single element means losing access to your funds. While you could duplicate your seedphrase and stash copies throughout your home, this approach increases the risk of theft significantly.
Bottom Line
Choosing between singlesig and multisig necessitates a thorough understanding of one's technical proficiency, risk tolerance, and security requirements. While multisig offers unparalleled security benefits, it demands expertise and careful management.
Singlesig, on the other hand, provides simplicity but at the expense of heightened vulnerability to single points of failure. At the end of the day, the decision hinges on aligning security measures with individual capabilities and preferences.
Frequently Asked Questions (FAQ)
What is the difference between Multisig and Singlesig?
Which one is more secure: Multisig or Singlesig?
What are the benefits of using Multisig?
What are the disadvantages of using Singlesig?
Can Singlesig be upgraded to Multisig?