Public And Private Keys: What Are They And How Do They Work?
In this article I will explain why public and private keys play such a vital role in Bitcoin (and other crypto). In fact, they enable direct transactions without the need for intermediaries or third-party verification. These keys are an integral part of the public-key cryptography system.
Before going into the individual concepts of public and private keys, it is essential to discuss the fundamental concept of public key cryptography.
Public key cryptography, also known as asymmetric cryptography, is a cryptographic system that uses a pair of mathematically related keys to secure communications and ensure the confidentiality, integrity, and authenticity of data exchanged over untrusted networks such as the internet. It is widely used in various applications, like email, web browsing, digital signatures, and secure data transmission.
In public key cryptography, each participant generates a pair of keys: a public and a private key. The public key is made freely available to others, while the private key is kept secret and known only to the owner. The two keys are mathematically linked, but it is computationally impossible to derive the private key from the corresponding public key.
The public key is used for encryption and verifying digital signatures, while the private key is used for decryption and creating digital signatures. This duality allows for the secure exchange of information without the need to share the private key itself. It forms the basis of secure communication in a network where participants can trust each other's public keys but not their private keys.
| Term | Definition |
|---|---|
| 🔒 Public Key | A cryptographic key openly shared for encryption and verification of digital signatures. |
| 🔐 Private Key | A confidential key used for decryption and creating signatures, to be kept secret. |
| 📝 Encryption | The process of transforming data using a public key, ensuring it can only be decrypted with the corresponding private key. |
| 🔍 Verification | The process of confirming the authenticity and integrity of data or transactions using public keys. |
| 🤝 Key Exchange | The secure sharing or establishment of a shared secret key between two parties using public key cryptography. |
Public Key Cryptography: An Example
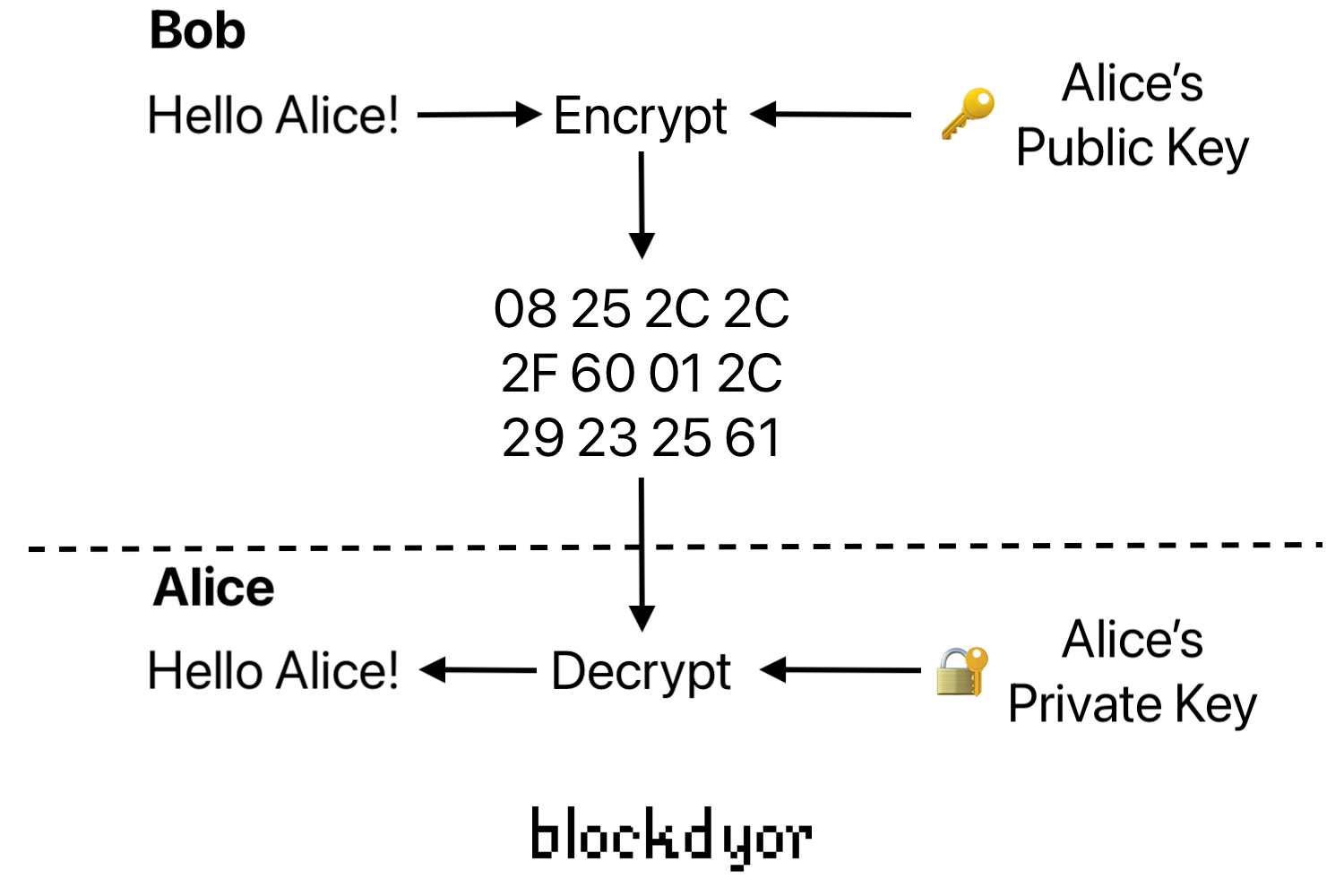
To make the process easier to understand, let's consider a scenario where Alice wants to send an encrypted message to Bob using public key cryptography:
- Alice creates a key pair: a public key and a private key. She shares her public key with Bob or makes it available to anyone who wants to communicate securely with her.
- Bob obtains Alice's public key and uses it to encrypt the message he wants to send. The encryption process transforms the plaintext message into ciphertext, which is unintelligible to anyone without the corresponding private key.
- Bob sends the encrypted message to Alice over an untrusted network.
- Upon receiving the ciphertext, Alice uses her private key to decrypt it and recover the original plaintext message. The decryption process ensures that only Alice, as the possessor of the private key, can read the message.
Public Key
A public key is a crucial component of public key cryptography. It is a unique and openly accessible cryptographic key that is part of a key pair. Unlike the private key, which must remain confidential, the public key is meant to be shared with others. It serves as a recipient's address in cryptocurrency transactions or as a means to verify digital signatures.
With a public key, one can safely send data or funds to the corresponding private key holder without the need for a middleman or third party. The public key has an important role in ensuring secure and transparent communication in various cryptographic systems.
Private Key
A private key is the other super-important element of PKC, forming a key pair along with the public key. It is a confidential and securely stored cryptographic key known only to the key owner. Unlike the public key, which is shared with others, the private key must be kept secret to maintain the security of the system.
The private key is used for decrypting data encrypted with the corresponding public key and for creating digital signatures. It enables the key owner to access and control the resources associated with the public key, such as cryptocurrency funds or encrypted messages.
It is of utmost importance to safeguard the private key to prevent unauthorized access. If an unauthorized person gains access to the private key, they could potentially impersonate the key owner, decrypt confidential information, or gain control over sensitive assets.
Private and Public Keys in Cryptocurrencies
When it comes to Bitcoin and other cryptocurrencies, your private keys are securely stored within a cryptocurrency wallet. These wallets can take the form of software applications like Sparrow Wallet or specialized hardware devices such as the Trezor Model T. Importantly, your private keys are not stored on the cryptocurrency blockchain network itself.
If you choose to keep your cryptocurrency on an exchange such as Binance or Coinbase, the exchange serves as the custodian of your private keys. In this scenario, you place your trust in the exchange, similar to how you would trust a bank to safeguard your gold in their vault.
However, if you transfer your cryptocurrency to a non-custodial wallet, you regain control of your private keys. In this case, the configuration and functionality of cryptocurrency wallets typically handle the management of private keys automatically, reducing the need for you to directly interact with them. Instead, you are often provided with a seed phrase that acts as a backup and encodes your private keys.
By using the seed phrase, you can restore access to your private keys if needed. This approach offers convenience and security, ensuring that even if you don't directly handle the private keys, you still have the ability to control and protect your cryptocurrency assets.
How Public and Private Keys Work Together
Understanding the interaction between public and private keys is crucial for comprehending how cryptocurrency transactions operate. When you claim to be the owner of cryptocurrency, what you truly possess is a private key that serves as proof of ownership (means you can spend it).
The private key, must be kept secure and is not disclosed or stored on the blockchain. They public and private keys are cryptographically connected in such a way that you can derive the public key from the private key, but you cannot take the public key and derive its paired private key.
How a Private Key Is Created?
The generation of a private key typically occurs inside a user's wallet. Bitcoin or other crypto wallets employ an industry-standard method for generating private keys. The process begins with the wallet utilizing a secure random number generator to create a seed.
This seed serves as the base for deriving multiple private keys as required by the user. This approach offers a convenient backup solution for wallets since only one seed needs to be securely stored instead of individually safeguarding each distinct private key.
By using a secure random number generator and a seed-based derivation process, cryptocurrency wallets ensure the generation of private keys that are sufficiently random and resistant to predictability. This ensures the overall security of the cryptographic system and helps safeguard the user's assets and sensitive information associated with the private keys.
Signing A Bitcoin Transaction Using the Public and Private Keys
To perform a transaction on the blockchain, it is necessary to follow a signing process. Here are the steps involved when someone intends to send you a transaction:
- Transparency: There is no encryption, as the transaction data is secured through digital signatures. The details, including the amount, sender address, and receiver address, are visible on the blockchain, ensuring transparency. Digital signatures, created with the private key, provide authentication and integrity to the transaction without relying on encryption for confidentiality.
- Signature: The encrypted transaction is then signed using your private key. This signature serves as proof that the transaction has not been tampered with during its journey. The digital signature is generated by combining the private key with the transaction data.
- Verification: The recipient of the transaction, along with the network nodes, can authenticate the transaction's authenticity using the associated public key. By verifying the digital signature against the public key, the network ensures that the transaction has been signed by the legitimate owner of the funds.
By digitally signing a transaction, you provide evidence of your ownership of the funds being transferred. The network's nodes automatically check and authenticate transactions.
Any transactions that fail to be authenticated are rejected by the network. Once a transaction is successfully authenticated and mined onto the blockchain, it becomes irreversible.
This signing process, coupled with verification by the network, guarantees the integrity and security of transactions on the blockchain, maintaining the trust and immutability of the decentralized system.
Bottom Line
Understanding the meaning of public and private keys is quite important in the fields of cryptography, but also cryptocurrencies like Bitcoin. Public key cryptography forms the foundation of secure communication and transaction verification, allowing for confidentiality, integrity, and authenticity in data exchange.
Public keys serve as unique identifiers and can be shared openly to receive transactions or verify signatures. On the other hand, private keys must be kept confidential as they grant access and control over associated assets. With public and private keys working together, individuals can securely send and receive funds without the need for intermediaries.
The choice between managing one's own keys or trusting a custodian depends on personal preferences and risk tolerance. It is crucial to prioritize security when selecting custodial solutions and to safeguard private keys when managing them independently.