OpSec: How To Protect Your Identity & Crypto
As time progresses and your wealth grows, there comes a point where strengthening your privacy and addressing security vulnerabilities in your daily life becomes a priority. This guide delves into my Opsec process, sharing tips and introducing services that I utilize to enhance my personal privacy.
Operational security (OpSec) is a term now widely employed in the realms of cybersecurity, online privacy, and cryptocurrency. In a broader context, it means safeguarding the data involved in a process or operation against potential adversaries, such as cybercriminals or rival entities, who could exploit or misuse it.
In the information age, protecting one's privacy is increasingly challenging, given the virtually infinite memory of the internet and the growing reliance on technologies like cloud computing to handle critical data.
This guide will be organized into sections, progressing from basic to advanced strategies to enhance privacy, security, and the protection of crypto assets.
👉 Click here to get the Bitkey. Use code BITKEYBLOCKDYOR at checkout for an exclusive 10% discount.
Why Privacy Protection Matters

You might wonder, "I comply with tax regulations and follow the rules, so why bother safeguarding my privacy and assets?"
It is crucial to exercise extreme caution regarding privacy because establishing it takes time, but it can be lost in an instant, and recovering the same level of privacy is often difficult.
Consider the scenario where someone discovers the amount of Bitcoin in your wallet; this information could make you a target. The story of the $5 wrench attack emphasizes the vulnerability of individuals, especially as wealth increases or when expressing certain political opinions or post some remarks on social networks, as seen in the case of Hodlnaut.
From March 2019 onward, spanning several years, Hodlnaut, a Norwegian bitcoin enthusiast, confronted a privacy crisis during his clash with an Australian programmer—referred to as CSW for brevity. After Hodlnaut criticized CSW claims to be Bitcoin's creator, CSW retaliated by seeking Hodlnaut's identity.
CSW team engaged in an aggressive investigation, ultimately doxxing Hodlnaut by revealing his real name and workplace. This invasion of privacy led to legal battles in Norway, where Hodlnaut defended his right to free speech. Despite being outnumbered, Hodlnaut's legal team, supported by crowdfunding, won in Oslo's court.
I won. Welcome to law.
— hodlonaut 80 IQ 13%er 🌮⚡🔑 🐝 (@hodlonaut) October 20, 2022
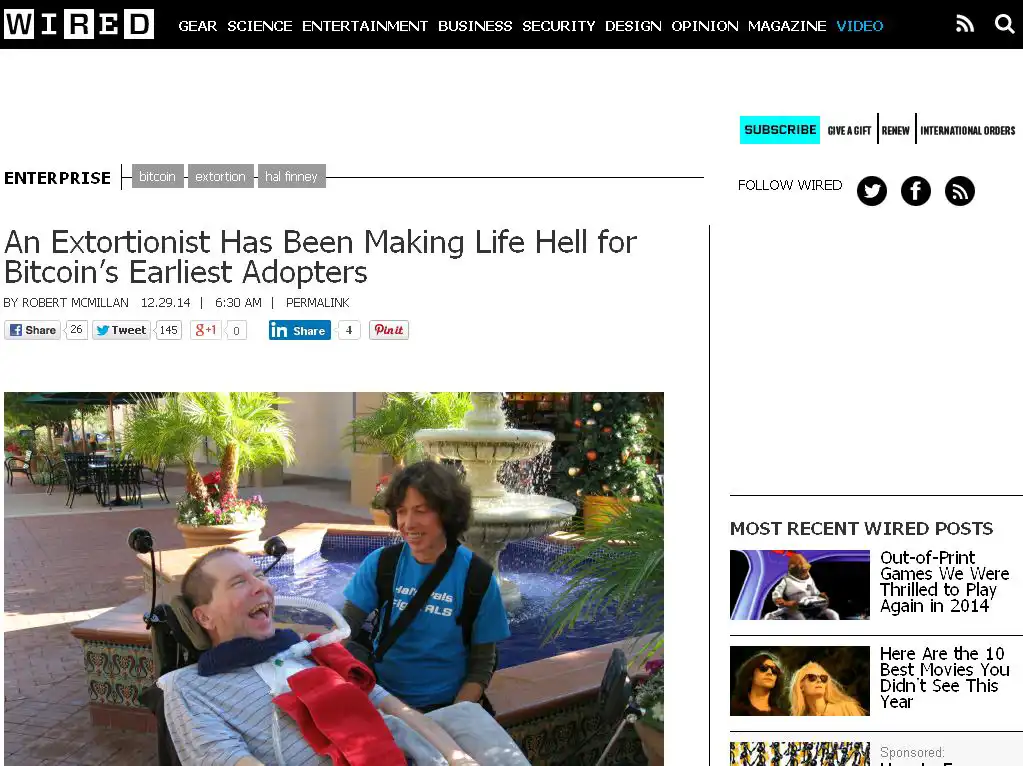
There are other countless examples, but probably the most dramatic one is the store of the extortionist that has been making life hell for Bitcoin’s Legend and earliest adopters: Hal Finney. Hal, a computer cryptography expert battling Lou Gehrig's disease, and his wife Fran experienced a swatting incident during which a caller falsely claimed to have committed a heinous crime, prompting a SWAT team response to their Santa Barbara home. The caller had been demanding a 1,000 bitcoin extortion fee for a year.
The Hodlnaut and Finney cases prompts reflection on personal safety. If you were in a similar situation, would you be willing to fortify your home, install security cameras, implement a comprehensive security system, change jobs, relocate, or even consider changing countries?
There is no one-size-fits-all solution to such challenges; the response must be tailored to individual needs and comply with the laws of the country of residence. Personalized and region-specific strategies are essential for mitigating risks and ensuring a balance between privacy and security in an increasingly interconnected world.
Levels of Privacy

This guide won't give you with the skills to vanish from the world or assume a new identity in a quaint New Hampshire cabin—those are beyond its scope. However, it will illuminate steps to reach optimal privacy and security for both you and your assets while maintaining your current reputation.
There are four primary levels of privacy protection:
- Privacy for the Average Joe:
- Aimed towards countering individuals familiar with basic internet searches.
- Suitable for those seeking fundamental privacy measures.
- Privacy against Resourceful Adversaries:
- Geared towards countering individuals with the means to hire an economic investigator.
- Provides enhanced protection for those facing adversaries with more resources.
- Privacy Shield against Well-Funded Opponents:
- Tailored for individuals up against adversaries with significant financial resources, capable of hiring top-tier private investigators.
- Offers advanced privacy measures for heightened security.
- Privacy Fortification against Nation States:
- Designed for individuals under the potential scrutiny of nation states with virtually unlimited resources.
- Involves robust privacy strategies against the highest level of threat.
For most readers seeking to safeguard their bitcoins or other altcoins while ensuring personal privacy and safety, the focus will likely be on the first two levels. This guide will be basically dedicated on these aspects.
However, if your concern extends to protection against nation-state threats or scenarios reminiscent of Edward Snowden's revelations, regrettably, such comprehensive protection is quite beyond the purpose of this guide.
Keep a Low Profile

Some individuals enjoy bragging about their real estate, cryptocurrency holdings, cars or other possessions whether with friends or, unfortunately, online.
Unless you're a public figure obligated to disclose crypto holdings due to professional reasons (e.g., a crypto exchange CEO), there's no imperative need to reveal the extent of your holdings. Personally, I wouldn't share such information even to my closest friend because, in most cases, it won't change their understanding on the topic.
At blockdyor, as media partners also with Bitcoin conferences like BTC Prague, we encourage attendance for the excellent networking opportunities they offer. However, it's crucial to be vigilant at these events, recognizing the potential presence of bad actors.
Similar caution should be exercised in local Bitcoin groups—while these gatherings are perfect for networking and forming new connections, it's essential to be selective about sharing details and avoid disclosing your holdings.
A low profile is your best strategy. Blend into the crowd, strive to be inconspicuous, and remember, the wealthiest individuals often don't flaunt opulence through extravagant clothing or exotic cars.
Protect Your Identity
As you live your life, building connections and friendships, it's not mandatory to share your personal infos. Consider adopting an alias or a pseudonym that can't be traced back to your real identity—a secondary persona. Opt for a common first and last name from your region to maintain simplicity.
Whether you're attending a party, a Bitcoin conference, or any event of your choice, there's usually no need to present your government ID. Ensure consistency in using the same alias to avoid confusion over time.
This precautionary measure allows you to engage socially without compromising your privacy, preventing potential mishaps or confusion regarding the pseudonyms you've shared with different individuals or services.

Protect Your Home
Ensuring the privacy of your residence is vital, acknowledging that your current dwelling, whether owned or rented, may already be compromised. Legal tactics come into play post-relocation to a new residence completely unlinked to your identity. Documents for this new address should not have the name of any individual or legal entity associated with you.
Laws in your jurisdiction might mandate being "contactable," aligning residency data with the actual living place. This registered residence typically follows the individual wherever they go. To conceal your current residence, you can move without notifying your municipality/state, maintaining the illusion of living in the old place.
An alternative method involves removal from the registry due to unavailability—an exceptional procedure initiated by the city townhall when a person is untraceable at the registered address after exhaustive attempts.
For better privacy, employing the shell or shelf company paradigm adds layers of legal entities to obscure asset ownership. Establish these entities to handle property transactions, utilities, and deliveries at your residence, creating a complex legal web that's challenging to unravel.
After relocating discreetly, be cautious during phone calls or video chats. Employ strategies like a collapsible background in your office and sound insulation to avoid inadvertently revealing your location during calls or videocalls.
Ensure photos posted online have their geolocation EXIF data removed, particularly those taken with a mobile phone. Timely online posts, regardless of the platform, can unintentionally disclose your location through temporal analysis, especially in less densely populated regions.
Protect Your Postal Mail
Receiving any form of mail or packages, especially crypto hardware wallets or other devices, directly under your name at your home address poses risks.
The mail you receive undergoes scanning and database entry, and some courier services may tamper with the contents. To enhance privacy and security:
- Use a second home or consider renting a cheap apartment for mail delivery, providing a legitimate address without raising suspicions.
- Leverage the assistance of a reliable lawyer to receive mail on your behalf. Additionally, explore the use of a ghost address, one distinct from your actual residence, for various purposes.
- Invest in a virtual address or remail service, and consider combining multiple services to create a layered, "onion routing" system for your physical mail. Each "hop" in the route only has knowledge of the preceding and succeeding hops.
- Obtain a Post Office Box or mailbox for added privacy.
By following these tips you should massively help to mitigate any possible association from the letters and items your receive and your real identity.
Protect Your Real-Time Location
Try minimizing location tracking by limiting the use of tracking devices, particularly on phones—although even if they are literally live-tracking devices, asking to eliminate them entirely may seem excessive. Instead, disable location services when unnecessary or, at the very least, turn off location history.
Even with GPS turned off, certain apps may still access location data through mobile network cell triangulation. For enhanced privacy, avoid using a Google or Apple account linked to your real identity on your phone. Opt for a disposable account for mobile use.
While in urban spaces, be mindful of surveillance cameras in public and private areas, functioning also as real-time location trackers.
Wearing full face masks or balaclavas to obscure your face may be illegal in some countries, and with the pandemic era behind us, even an surgical "covid" mask might draw unnecessary attention, unless you live in asian countries like Japan or Taiwan where they are heavily used.
A practical alternative is wearing a hat with a broad brim, such as a baseball cap, and complementing it with dark, mirrored "aviator" style glasses to cover a significant portion of your face. This strategy helps mitigate the risk of being visually identified in various surveillance scenarios.
Protect your phone
Many websites force users to provide a mobile phone number, often verifying it through SMS, posing a significant privacy concern. Revealing your personal phone number discloses your residing nation, and, in most cases, your mobile number is linked to your identity.
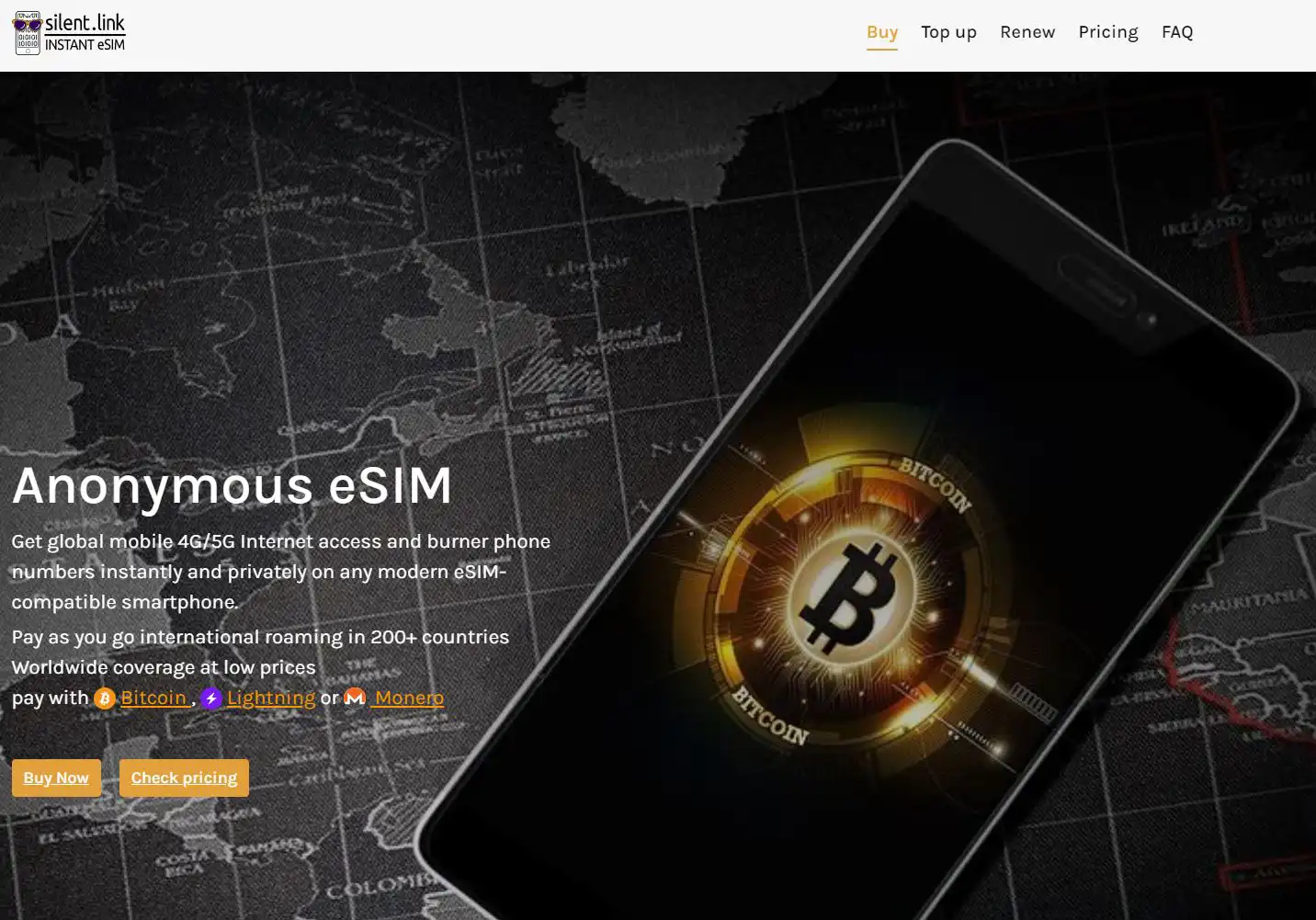
For online services and apps, it's advisable to use burner numbers purchased with cryptocurrency, ensuring anonymity without tying your identity to payment cards. Silent.Link is a service offering global mobile 4G/5G Internet access and burner phone numbers, enabling private registration without revealing personal details. They accept Bitcoin and other cryptocurrencies, facilitating a secure and discreet sign-up process.
By utilizing such services, you can establish a phone number unlinked to your identity, receiving SMS, calls, and other authentication methods for online private services.
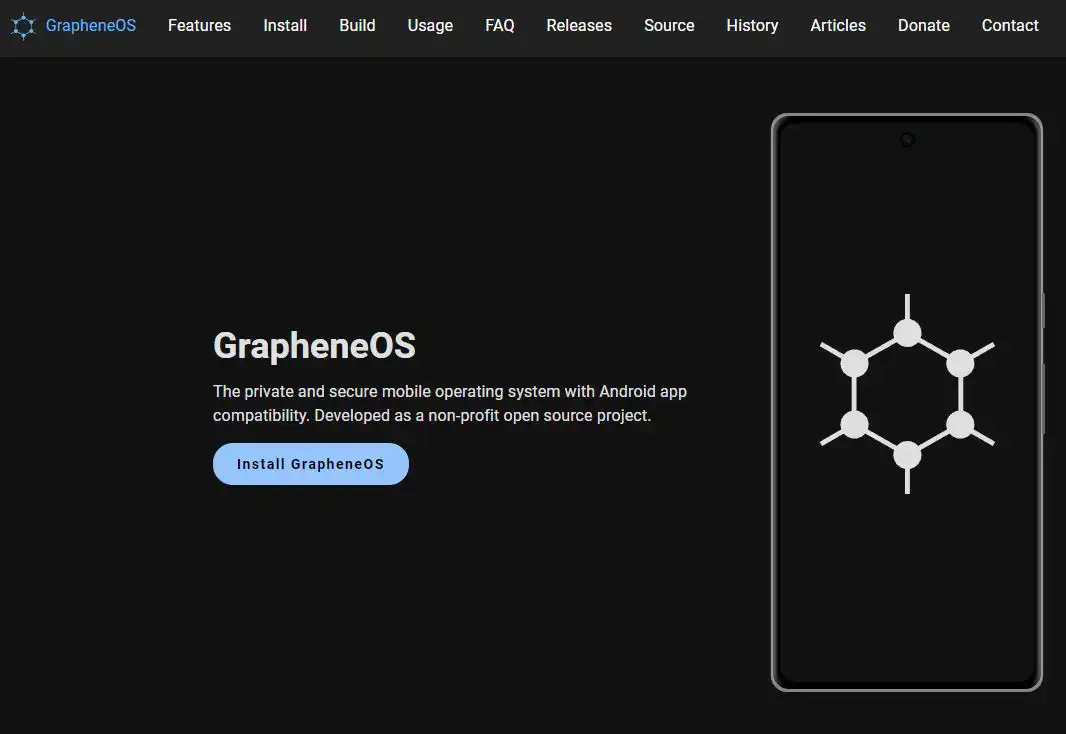
Additionally, consider using phones with more secure operating systems than iOS or Android, such as GrapheneOS. This open-source solution prioritizes privacy and security, implementing measures like enhanced app permissions, robust memory allocation, strengthened disk encryption, and more.
Notably, GrapheneOS does not include Google Play services, ensuring a heightened level of privacy. While Google Play services can be installed separately in a fully sandboxed manner via the sandboxed Google Play compatibility layer, GrapheneOS provides a comprehensive solution for those seeking privacy-focused mobile operating systems.
Protect Your Internet
Your Internet Service Provider (ISP), government, and various agencies may monitor the internet traffic originating from your home/office. Additionally, your computer and devices could harbor tracking software aimed at associating your online activity with specific interests for targeted advertising.
Using ad-blockers like uBlock Origin in your browser helps to mitigate unwanted tracking. uBlock comes with a default ad-blocking lists, but enhancing your protection with customized lists based on your country is advisable, accessible for free on platforms like Easylist.to.
For browsing, consider opting for TOR websites with the ".onion" domain whenever possible. TOR, a free service, offers increased security by keeping your IP private and routing your connection through three proxies. However, note that exit nodes can potentially observe all your traffic, a notable drawback of TOR.
An alternative, potentially more efficient than TOR, is using a VPN—a crucial tool for internet privacy. VPNs, like Proton VPN, prevent websites from accessing your real IP address, safeguarding your geographic location. It encrypts your traffic, protecting your data not only at home but also on public or less secure connections.
Choosing a VPN that also accepts cryptocurrency ensures anonymity, and Proton VPN accepts bitcoin.
This Swiss-based company, operates under stringent privacy laws, adheres to a no-logs policy, and offers an open-source solution. While available for free, paid plans provide additional features, making it a comprehensive option for securing your internet activities.
👉 Click here to get Proton VPN for free.
Protect your email
Using your primary email, for registering on crypto exchanges for example, especially non-KYC platforms, undermines the intended privacy of these services. Mainstream email providers often neglect user privacy, tying your email to your identity.
If you register with your main email on a non-KYC Bitcoin exchange like Hodl Hodl for example, and it's linked to your real name and other accounts, a breach could expose personal information.
A more secure approach is using a secondary email account, preferably fully encrypted, for private services. Opt for a pseudonym instead of your real name when you register to it.
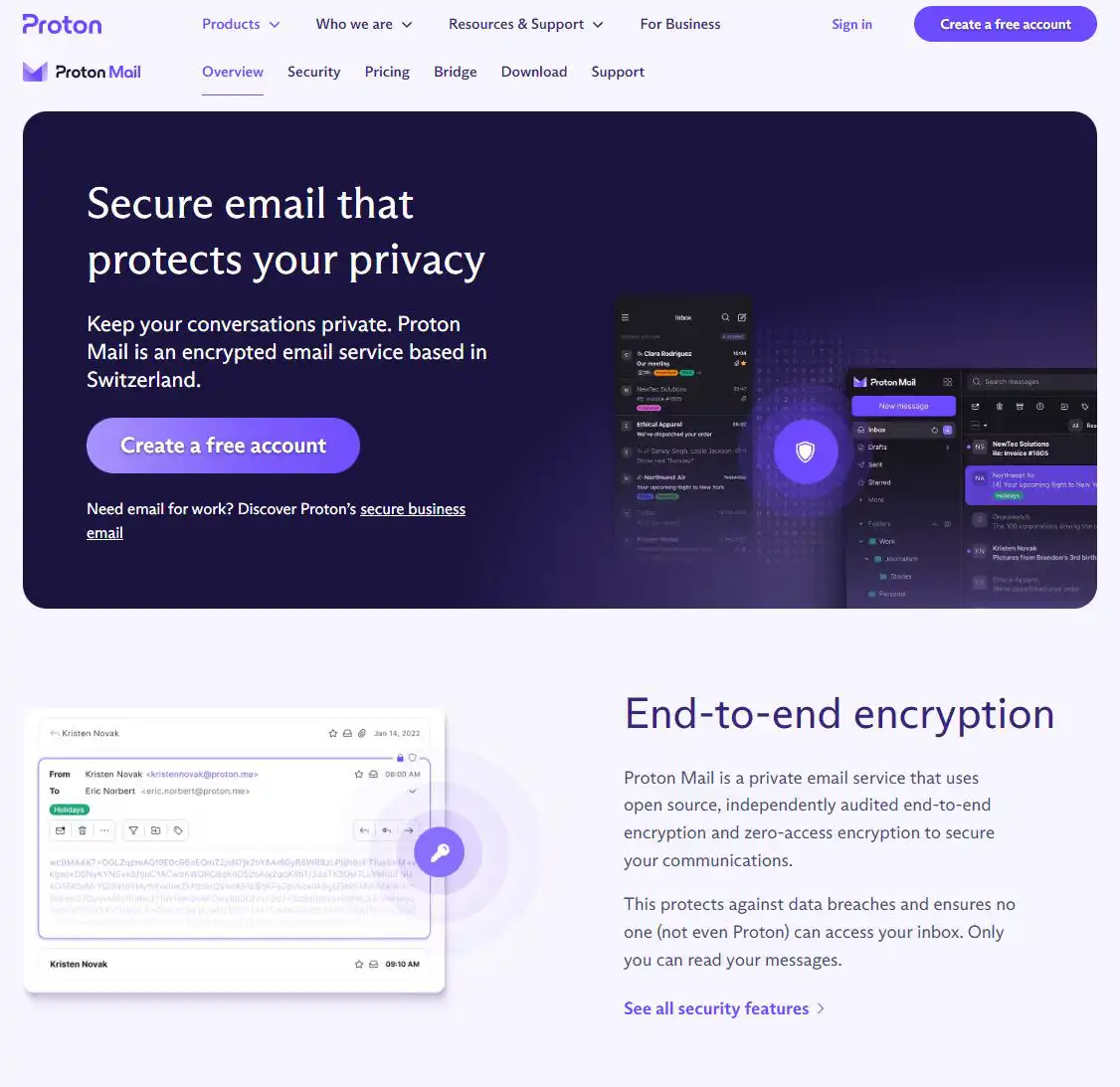
Proton Mail, a solution from the same Swiss company as Proton VPN, offers a reliable option. It's entirely open source, transparent, and encrypts all your emails for enhanced security. You can start even with a free account without KYC or opt for a paid plan, and even pay in bitcoin for additional storage and features. This ensures an added layer of anonymity and protection for sensitive information.
👉 Click here to get Proton Mail for free.
Secure Your Computer
There is no second best webcam cover. @Blockstream #Bitcoin #LiquidNetwork pic.twitter.com/LISX0cCnAN
— blockdyor (@blockdyor) December 17, 2023
The Blockstream webcam cover
Enhance your privacy by covering your laptop webcam with a tape or by getting a sliding shutter, as some malware can exploit it to record your activities.
Opt for open-source operating systems like Ubuntu instead of Windows or MacOS for increased security. Employ a firewall such as Little Snitch to manage both incoming and outgoing connections.
Regularly format your computer and scrutinize installations to prevent malware, including keyloggers that capture keystrokes and transmit them to malicious actors. This is especially crucial for those using computers for Bitcoin or crypto wallets, where a keylogger could compromise sensitive information like seed phrases.
Protect Your Accounts
Diversify your online account passwords to avoid a single point of failure. Prioritize securing your email account(s), as they are often used for password recovery.
Instead of using the same password across all accounts, employ a secure password manager with encryption, like Bitwarden, generating unique strong passwords for each service.
For added security, implement two-factor authentication (2FA) on every online account. Consider using dedicated 2FA hardware devices like Yubikey for an extra layer of protection.
Secure Your Instant Messaging (IM) Apps
Be cautious when sending text messages, phone calls, or emails, especially in public networks, as they can be intercepted without end-to-end encryption.
While apps like WhatsApp, Telegram, and Signal offer encryption, they typically require a phone number. For added privacy, consider associating a different SIM card than your usual one with these apps.
Although these apps operate within centralized environments, the built-in encryption enhances privacy. To maximize confidentiality, avoid linking them to your primary phone number. If utmost privacy is desired, consider using these apps on a burner phone instead.
I prefer the secure instant messaging app Keybase, which is compatible with Linux, Mac, Windows, and mobile devices and doesn't mandate a phone number for usage. Keybase employs public key cryptography, the same security mechanism used in bitcoin, to safeguard the privacy of your messages.
The encryption is so robust that even Keybase itself cannot access the content of your chats. It serves as an excellent platform to maintain privacy while also offering an opportunity to understand the basics of PGP. Feel free to follow blockdyor on Keybase below!

Protect Your Purchases
While cash remains an excellent method for maintaining high privacy, its acceptance is decreasing, especially in online transactions where it's impractical. Cryptocurrencies, such as Bitcoin, serve as an alternative that severs the link between financial identity. Bitrefill emerges as a notable use case for crypto in online purchases.
Bitrefill offers a service allowing users to purchase gift cards from thousands of online and physical merchants using cryptocurrencies like Bitcoin and Ethereum. I know some people that actually live on crypto day by day thanks to Bitrefill.
Notably, it operates on a non-KYC (Know Your Customer) basis, empowering individuals to leverage the purchasing power of their cryptos for acquiring gift cards in complete anonymity. These cards can then be utilized both in-store and online, promoting a cycle of reuse for enhanced privacy.
👉 To join Bitrefill and unlock the power of living on crypto, click here.
Secure Your Taxable Property

Your property, encompassing real estate, cars, and businesses tied to your name, creates public records, presenting a potential privacy leak that requires mitigation.
In some countries, ownership of a car can be easily verified by entering the plate number into an online database. To maximize privacy, consider establishing an LLC or legal entity unlinked to your identity.
For liability and privacy reasons, it's advisable to have separate LLCs for real estate and vehicles. This approach reduces the connections to your residence, preventing attackers from easily linking your various assets through a common legal entity.
When dealing with vehicles, opting for commercial fleet insurance can keep your name off the insurance policy
If establishing an LLC or legal entity unlinked to your identity is not feasible due to resource limitations, you can explore alternatives such as renting or leasing a car. In these arrangements, the ownership of the car typically belongs to the renting company, and insurance is often included.
Protect Your Identity While Traveling

If you're traveling in a car registered under your name, take extra precautions to safeguard your privacy. Check for installed GPS devices in your vehicle, and consider purchasing or renting cars without such tracking mechanisms. For enhanced anonymity, consider registering the vehicle under an anonymous LLC.
Crossing international borders exposes your privacy to potential risks. Avoid carrying sensitive data, such as cryptocurrency private keys stored in a hardware wallet, when crossing borders. If you only have unencrypted devices with you, border agents won't uncover any confidential information.
When staying in hotels during your travels, consider using a pseudonym for reservations to protect your identity. While it was once simpler to use any name and pay with cash, most hotels now require an ID and a credit card. To overcome this, add an "authorized user" to your existing credit card under the pseudonym you prefer. Make the reservation and payment using that pseudonym, and during check-in, present your real ID.
Since the reservation is under a different name, it typically won't pose an issue. This practice is common among professionals like authors, actors, and musicians, who use their stage name for reservations to maintain privacy. If questioned, explain that the reservation is under your professional name because your credit card was issued under that name.
Protect Your Crypto
To safeguard your cryptocurrency and privacy, a highly recommended approach is to utilize non-KYC exchanges that facilitate Bitcoin purchases with cash. This method offers a secure means of acquiring crypto without tying it to your identity.
Azteco is a notable solution available globally, offering a safe and private option to buy Bitcoin with cash in many points around the globe. In Canada, Bull Bitcoin provides a convenient way to purchase BTC with cash at the post office. To increase the anonymity of your non-KYC coins, you might want to mix these coins with services like Whirpool and Wasabi (Coinjoin).
While there are alternative No-KYC solutions for buying Bitcoin using different payment methods, it's crucial to note that using cards or bank accounts, even without KYC, may still establish a link between your identity and the coins.
Based on years of experience, the most effective way, at least for some, to store Bitcoin is by using air-gapped devices. These devices never connect to the internet or a computer and are ideal for securely storing private keys and signing transactions when necessary. Devices like the Blockstream Jade, Coldcard or Passport have been reviewed positively over the years.
For a backup of your seed phrase, which is essentially the mnemonic version of your private key, engraving it on metal is a prudent choice for durability and longevity. The Cold Wallets by Black Seed Ink offers a reliable and user-friendly solution for this purpose.
Run your own node
For Bitcoin users, running your own node is a crucial step. By doing so, you actively participate in the economic validation of your (and others) transactions in the Bitcoin decentralized network, significantly enhancing your privacy.
When you run your own node, you connect within your personal network, shielding your addresses and, more crucially, your Xpub from external visibility. This not only fortifies your privacy but also contributes to decentralizing the network, making it more robust.

Generate Misleading Information About Yourself
If you have the means to do so, consider creating fictitious infos about yourself to establish deceptive trails.
For instance, leaking incorrect data about your residency can potentially mislead individuals attempting to find or gather information about you, adding complexity to those intruding into your privacy zone.
Here's a suggested solution:
- Select a country or city where you could potentially relocate.
- Inform friends who never or rarely visit that this is your new location.
- Update all your social networks with this new location data, indicating your presence there.
- Share authentic-looking posts with photos portraying you in the supposed location.
- Establish a new website containing these fabricated details about you and link your social networks to it.
This strategy serves as an effective method to make life more challenging for potential attackers, potentially discouraging them from persistently attempting to locate you.
Reduce Your Digital Footprint

If you've ever searched for yourself online and found personal details like your name and home address on unfamiliar sites, here's how to put a stop to it.
- First, consider getting a throwaway email for this process to avoid using your main one with these sites. Avoid sending unnecessary verification data, especially licenses, to prevent bolstering their profiles about you.
- Consider freezing your credit with major and smaller bureaus, ensuring to selectively unfreeze for specific creditors when necessary. This added layer of protection prevents the sale of your data without hindering your ability to use credit.
- Additionally, add a fraud alert to your credit history or selectively freeze it for specific creditors if you plan to apply for credit or a loan.
- To control data shared with marketing entities, register with OptOut Screen and DMAchoice.
- Opt-out of data sharing with credit and debit card companies by calling their provided 1-800 number.
- Suppress your information from public databases by contacting your municipality if you own property.
- Opt-out of Equifax's salary sharing database, The Work Number, by calling them and requesting removal for each employer.
- Consider the public nature of home address information when registering to vote or changing your address with the USPS.
- Change your email addresses regularly and use aliases, especially for social media.
- Review and opt-out of targeted advertising and other privacy-invading practices in service provider privacy policies.
- Change your email address every 1-2 years to make it challenging for data brokers to build a comprehensive profile.
- Lastly, periodically search your name, street number, city combination in different search engines to locate and opt-out from background check sites.
By taking these steps, you can actively reduce your digital footprint, minimize junk mail, and enhance your overall privacy online. Stay informed by regularly checking reliable sources for updates.
Bottom Line
As evident from this guide, implementing countermeasures in your daily activities can effectively minimize your digital footprint. However, it's crucial to recognize that these techniques may not fully evade the panopticon constructed by nation-states and government agents, leaving a legal trail of breadcrumbs.
Despite efforts to reduce your footprint, pervasive networked surveillance cameras in urban environments make complete avoidance of Big Brother's eyes challenging. Assume that data streams from these cameras are being collected and analyzed through various recognition algorithms.
Equally important is scrutinizing the trustworthiness of individuals and services in your life, treating them as potential security vulnerabilities. Regularly review the information shared with service providers.
After setting up your privacy measures, if you feel to and have the resources, consider hiring a private investigator to test your OpSec and uncover any overlooked trails.