Bitcoin Wallet: The Complete Guide
Discover how Bitcoin wallets unlock financial freedom, safeguard your funds, and avoid costly mistakes—some secrets every Bitcoin hodler must know.
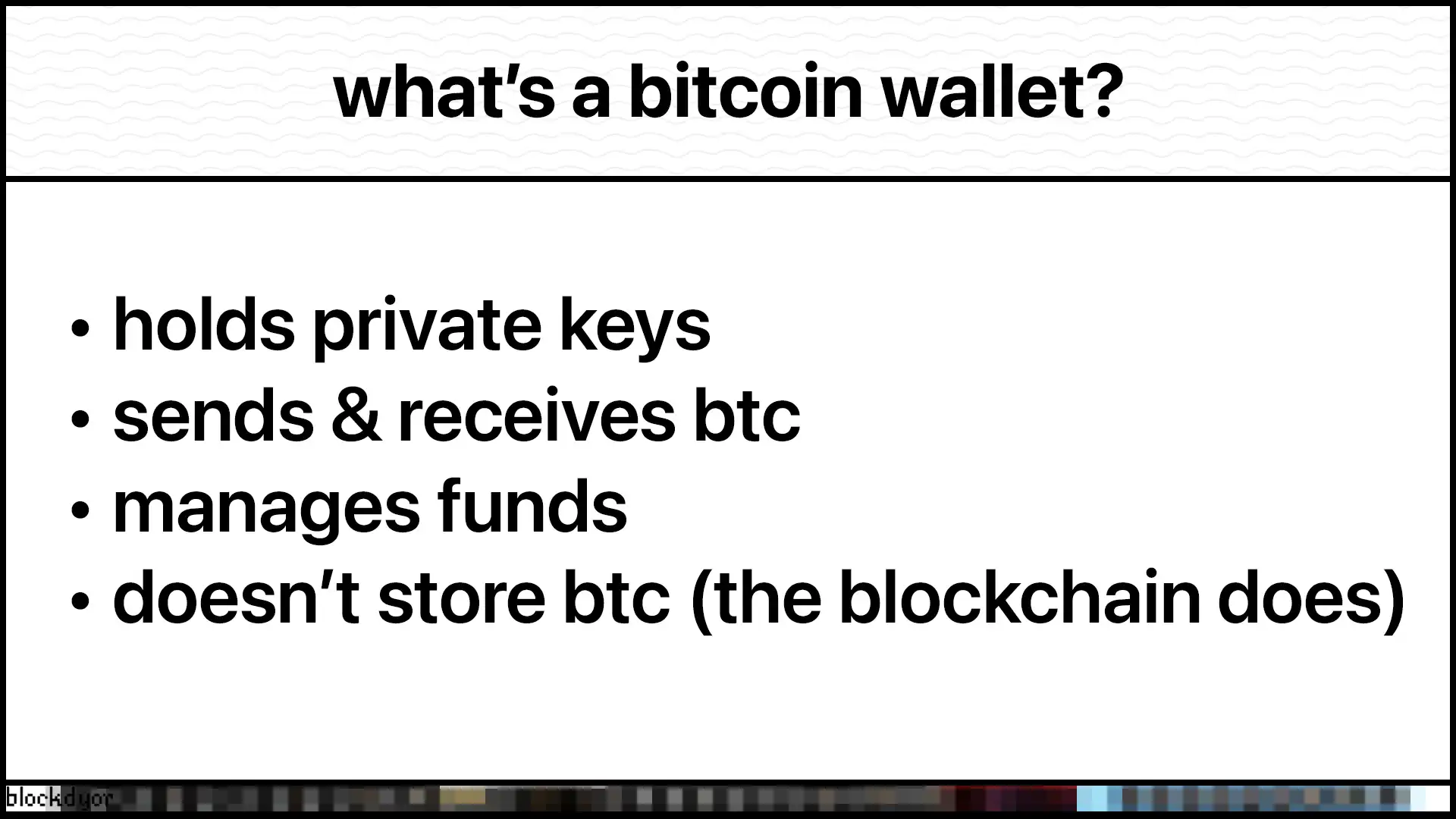
What’s A Bitcoin Wallet?
A Bitcoin wallet is a digital tool that allows users to store, send, receive, and manage Bitcoin (BTC) by securely storing and managing private keys. Here are the key aspects of Bitcoin wallets.
The Purpose of a Bitcoin Wallet
👉 Click here to get the Bitkey. Use code BITKEYBLOCKDYOR at checkout for an exclusive 10% discount.
Bitcoin wallets do not actually store Bitcoin itself (they are in the timechain/blockchain instead), but rather hold securely private keys that provide access to Bitcoin UTXOs on the blockchain. These wallets enable users to:
- Send and receive Bitcoin
- Manage bitcoin accounts
- Control access to blockchain funds
Types of Wallets
There are two big categories of Bitcoin wallets:
| Type | Characteristics | Security | Cost |
|---|---|---|---|
| Software Wallets | Installed on mobile/computer | Lower security | Free |
| Hardware Wallets | Physical devices | Higher security | Requires purchase |
Software wallets can be subdivided into mobile, desktop, and web-based applications, while paper wallets (physical document storage) constitute a distinct category that falls outside this basic classification framework.
Key Security Features
The primary function of a hardware wallet is to sign transactions, but it also offers a variety of additional features that enhance its utility and security.
- Private Key Management: A private key is a unique string of characters that allows access to a specific Bitcoin account. It is usually stored securely in the secure element chip of the wallet.
- Public and Private Key Pairs: Wallets generate multiple key pairs for managing your funds.
- Secure Access: Most of the wallets offer biometric and PIN protection.
Recommended Wallet Characteristics
When you are in the market for a Bitcoin wallet, look for:
- Works with any third-party wallet (vendor agnostic, no official one required)
- You hold your own keys (no middleman control)
- Adjustable transaction fees (choose speed/cost)
- Open-source code (transparent and auditable)
- Backup and recovery tools
- Strong security (protects your assets)
Some popular software Bitcoin wallets include BlueWallet (iOS/Android app), Sparrow Wallet (MacOS/Windows/Linux Desktop), and Proton Wallet (Web App).
For the hardware wallets airgapped we have the Foundaction Passport and Coldcard (single sig), and the Bitkey for the multisig.
Core Concept of Bitcoin Wallets
Bitcoin wallets represent a revolutionary digital mechanism for managing your funds, fundamentally different from traditional financial instruments. Unlike physical wallets or bank accounts, these digital tools provide users with direct, cryptographically secured access to their Bitcoin holdings through complex key management systems and, possibly, an easy to use UX.
Cryptographic Foundations: Private and Public Keys
The heart of Bitcoin wallet functionality lies in its cryptographic key infrastructure. Private keys are not just passwords but sophisticated mathematical constructs that provide absolute control over digital assets.
These unique, algorithmically generated strings represent the sole mechanism for authorizing Bitcoin transactions. Public keys, mathematically derived from private keys, serve as transparent, shareable identifiers that enable receiving transactions while maintaining the underlying asset's security.
This asymmetric cryptography ensures that while anyone can send Bitcoin to a public address, only the holder of the corresponding private key can access and transfer those funds.

Wallet Architecture
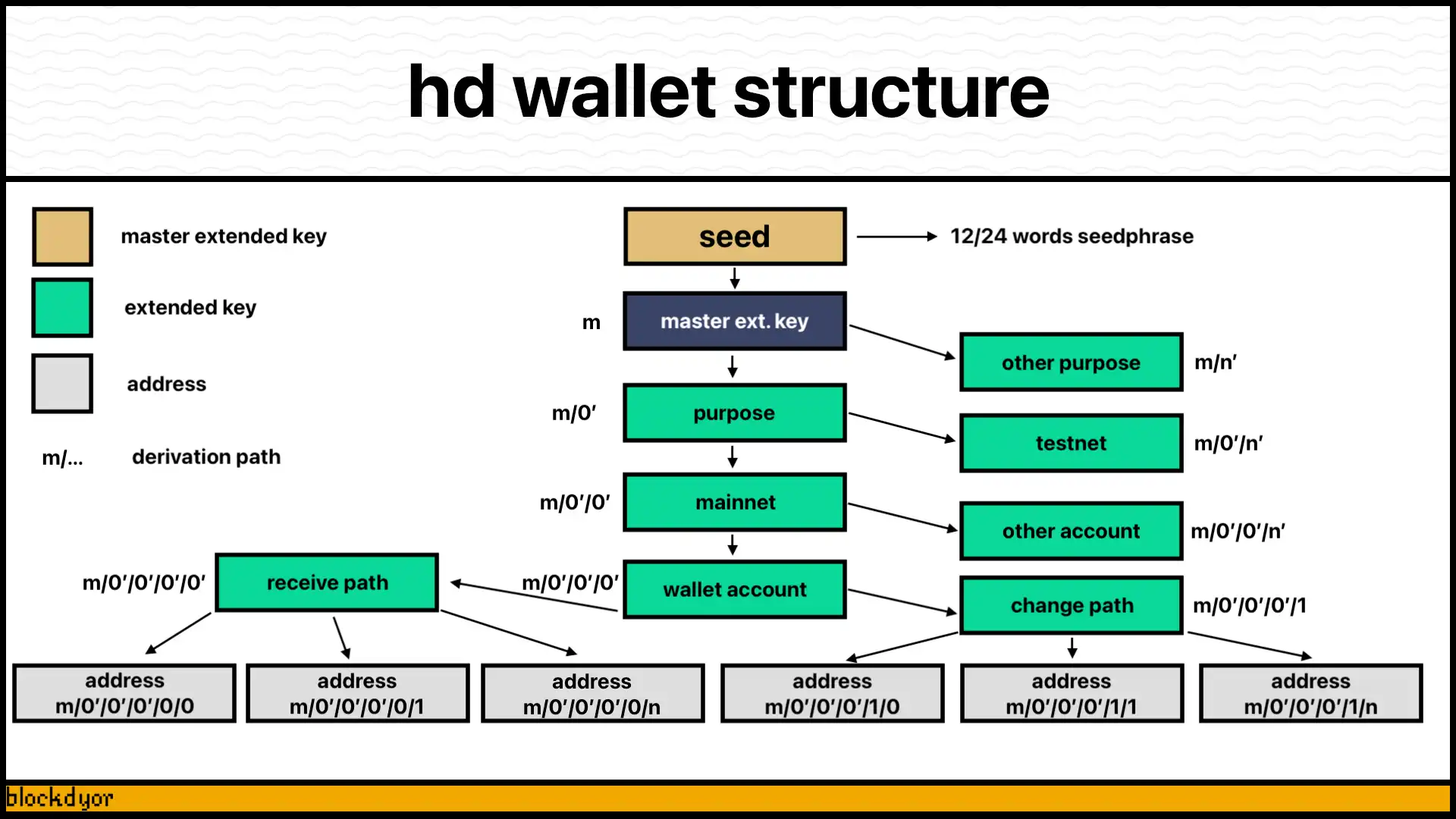
Modern Bitcoin wallets transcend basic storage concepts, implementing advanced technologies like Hierarchical Deterministic (HD) wallet structures. These sophisticated systems generate multiple bitcoin addresses from a single seed phrase, providing enhanced privacy, backup capabilities, and complex key management setups.
Transaction Mechanics
When a Bitcoin transaction occurs, it represents a complex choreography of cryptographic signatures and network verification. The wallet signs each transaction using the private key, broadcasting an encrypted message to the global Bitcoin network. Miners and nodes then validate this transaction, ensuring its authenticity and recording it permanently on the blockchain.
Security Philosophical Principles
Bitcoin wallet security extends far beyond technical implementations. It embodies a philosophical approach to financial sovereignty, where individuals maintain complete control over their digital assets without relying on centralized financial institutions. This paradigm demands personal responsibility, requiring users to understand and implement robust security practices.
Ownership Paradigm
Bitcoin wallets represent more than technological tools; they are instruments of financial and economic empowerment. By providing direct, intermediary-free asset management, they challenge traditional banking models and offer unprecedented individual economic autonomy.
Understanding the UTXO model
The Unspent Transaction Output (UTXO) model underlying Bitcoin transactions functions like a dynamic, digital change system. Each transaction creates specific inputs and outputs, tracking asset movement with mathematical precision and preventing double-spending.

How A Wallet Interacts With The Bitcoin Network
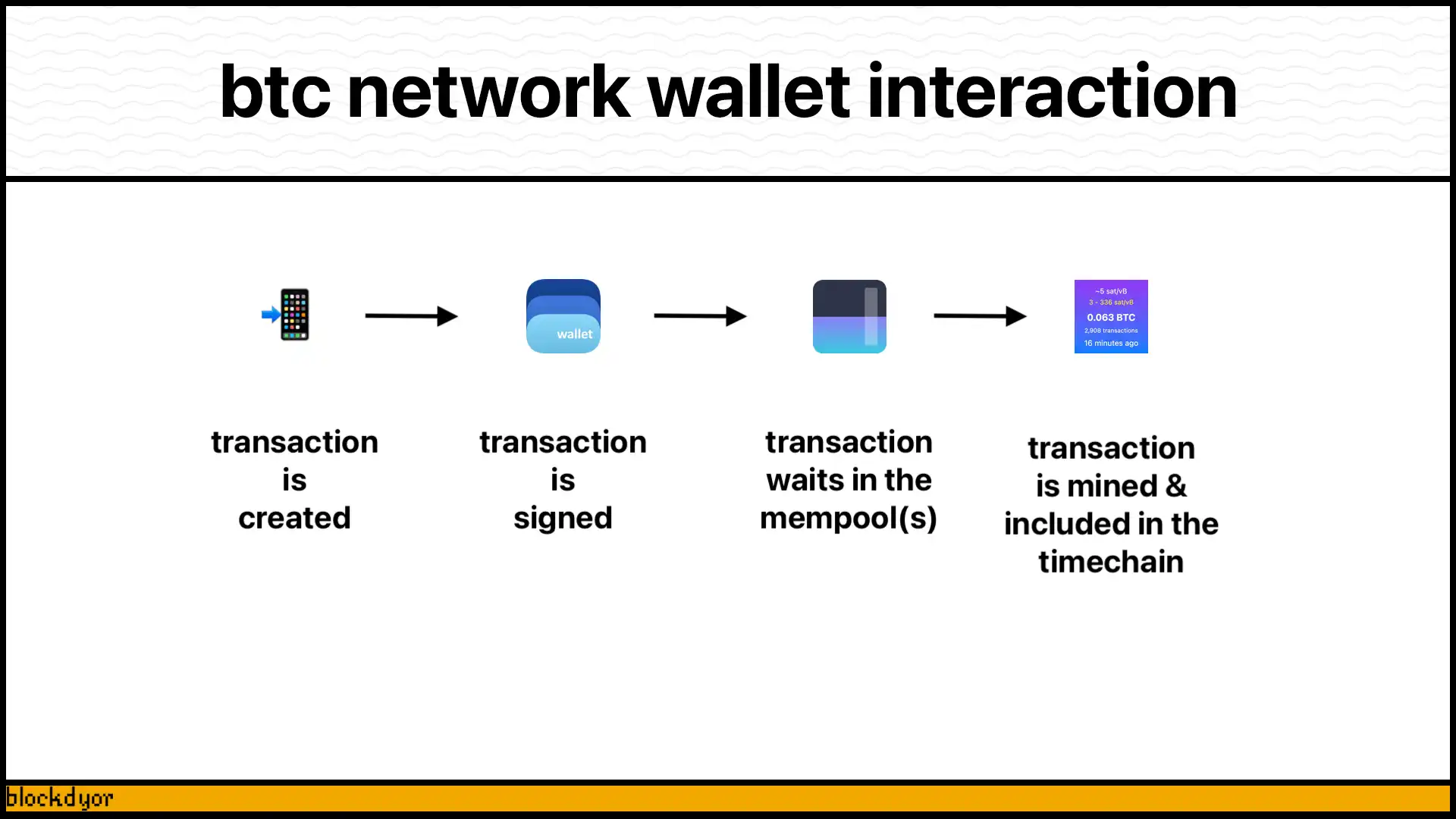
Bitcoin wallets interact with the bitcoin network through a sophisticated cryptographic communication process involving public and private keys. The interaction fundamentally relies on digital signatures and transaction broadcasting.
Transaction Initiation Process
When a user initiates a cryptocurrency transaction, the wallet performs several critical steps:
- Generate a transaction request with recipient address and amount
- Encrypt the transaction using the private key
- Digitally sign the transaction to prove ownership
- Broadcast the signed transaction to the nearest blockchain node
Node Verification Mechanics
The blockchain network receives this transaction through a distributed network of nodes, each acting as an independent verifier. These nodes perform an intricate validation process, examining the transaction's cryptographic signature, confirming the sender's available balance, and ensuring compliance with network protocols. This decentralized verification prevents fraud and eliminates the need for centralized trust mechanisms.
Mining and Block Validation
Miners play a crucial role in this ecosystem, selecting and aggregating validated transactions into blocks. By guessing a random number—a process known as proof-of-work—miners transform these transaction collections into permanent, immutable records on the blockchain. This computational effort ensures network security and prevents malicious manipulation.
Key Security Principles
The entire process represents a remarkable technological achievement: a system where financial transactions can occur securely, transparently, and without centralized control. Each transaction becomes a permanent, verifiable record, accessible to anyone yet controlled by no single entity.
Hot vs Cold Storage: Security Spectrum Analysis
The choice between hot and cold storage for bitcoin is fundamentally about balancing convenience and security. Understanding these two storage methods is essential for anyone looking to safeguard their digital assets effectively.
Hot Storage: Convenience at a Cost
Hot wallets are designed for ease of use, allowing users to access their cryptocurrencies quickly and efficiently. These wallets are connected to the internet, which enables instant transactions and seamless trading. Popular examples include mobile wallets like BlueWallet and web-based solutions such as Proton Wallet.
👉 Click here to get Proton Wallet.
The primary advantage of hot wallets is their convenience; they are ideal for day-to-day transactions and frequent trading activities.However, this connectivity comes with significant risks. Because hot wallets are always online, they are more susceptible to cyber threats, including hacking and phishing attacks.
Users must remain vigilant, as any lapse in security can lead to substantial financial losses. Therefore, while hot wallets provide immediate access to funds, they should be used primarily for smaller amounts or for transactions that require quick execution.
Cold Storage: Security Over Convenience
Cold storage refers to the practice of keeping private keys completely offline, ensuring they are never exposed to internet-connected devices. This method is widely regarded as the most secure way to store Bitcoin, particularly for long-term holdings, as it eliminates the risk of remote hacking or cyberattacks.
Cold storage solutions are ideal for users who prioritize security over convenience, as accessing funds requires additional steps, such as using PSBTs (Partially Signed Bitcoin Transactions) via SD cards or QR codes for transaction signing. While this approach may involve a steeper learning curve and slower transaction processes, it provides unparalleled protection against online threats. Cold storage is especially recommended for users holding significant amounts of Bitcoin or those who do not need frequent access to their funds.
Which One Is Better: Hot vs Cold
When choosing between hot versus cold storage, it's crucial to recognize that each method has a different point on the security spectrum. Hot wallets offer quick access and ease of use but expose users to higher risks due to their online presence. On the other hand, cold wallets provide enhanced security by keeping assets offline but require more effort to access (spend).
Many bitcoin hodlers adopt a hybrid approach, utilizing both hot and cold storage methods. This strategy allows them to enjoy the convenience of hot wallets for everyday transactions while safeguarding larger amounts in cold storage for long-term investment. By distributing assets across both types of wallets, users can effectively manage risk while maintaining flexibility in their bitcoin holdings.
Software Wallets: Subtypes and Use Cases
Software wallets are essential tools for managing cryptocurrencies, offering users the flexibility to store, send, and receive bitcoin with simplicity. They can be categorized into three main subtypes: mobile wallets, desktop wallets, and web wallets. Each type serves different use cases and user preferences, making it crucial to understand their unique features.
Mobile Wallets: App-Based Solutions
Mobile wallets are designed for users who prefer managing their cryptocurrencies on the go. These app-based solutions provide a user-friendly interface and are often equipped with features like QR code scanning for quick transactions.
BlueWallet is a prominent example of a mobile wallet that offers seamless Bitcoin management. It supports several functionalities, including multi-signature wallets and the ability to manage Lightning Network payments, making it ideal for users who frequently transact or need instant access to their funds.The convenience of mobile wallets comes with certain risks, as they are connected to the internet and can be vulnerable to hacking attempts. However, many mobile wallets implement robust security features such as biometric authentication and encryption to protect user data. For everyday transactions and quick access to funds, mobile wallets like BlueWallet are highly effective.
Desktop Wallets: OS-Specific Clients
Desktop wallets are software applications installed on a user's computer, providing a more secure environment compared to mobile wallets. They offer enhanced functionality and control over private keys since users can manage their wallets offline when not connected to the internet.
Sparrow Wallet exemplifies a desktop wallet that caters specifically to Bitcoin users. It offers advanced features such as coin control, custom transaction fees, and support for hardware wallet integration. Sparrow Wallet is particularly suited for users who prioritize security while still engaging in regular transactions. By keeping the wallet on a personal computer, users reduce the risk of exposure to online threats. However, it is essential for users to maintain good cybersecurity practices, such as using antivirus software and keeping their systems updated.
Web Wallets: Browser-Based Interfaces
Web wallets operate through internet browsers, allowing users to access their cryptocurrencies from any device with an internet connection. Proton Wallet is an example of a web wallet that emphasizes user experience while providing essential security features. Proton Wallet only supports Bitcoin (BTC) and does not offer compatibility with other cryptocurrencies.
Hardware Wallets: Offline Keys Storage

Signing devices or signers, often just simply called "Hardware wallets", are specialized tools designed to enhance the security of bitcoin holdings by keeping private keys offline, in "cold storage".
These devices, which typically resemble a small calculator or USB stick, provide a robust solution for safeguarding digital assets against online threats. By isolating private keys from internet connectivity, hardware wallets significantly mitigate the risk of hacking and unauthorized access.
Enhanced Security Through Isolation
The primary advantage of hardware wallets lies in their ability to store private keys in a secure, offline environment. Unlike software wallets that operate on internet-connected devices and are vulnerable to cyberattacks, hardware wallets ensure that sensitive information never touches the internet.
This air-gapped approach means that even if a computer is compromised, the private keys remain safe within the hardware device. Using a hardware wallet does require a slightly steeper learning curve compared to software wallets. Users must familiarize themselves with the physical device and its functionalities, which may include connecting it to a computer or mobile device for transaction verification. However, this added complexity is a small trade-off for the enhanced security these devices offer.
Types of Hardware Wallets
Hardware wallets can be categorized into two main types: single-signature and multi-signature wallets. Single-signature wallets, such as the Coldcard wallet, are straightforward devices designed for individual users who want to manage their Bitcoin securely. They allow users to generate and store their private keys offline while providing an intuitive interface for signing transactions.
On the other hand, multi-signature wallets, like Bitkey, require multiple signatures from different devices or users to authorize a transaction. This additional layer of security is particularly beneficial for organizations or individuals who want to implement shared control over their funds. By requiring consensus among multiple parties before any transaction can occur, multi-signature wallets significantly reduce the risk of unauthorized access.
Wallets Security Models
Understanding the various security mechanisms that protect bitcoin wallets is essential for users looking to safeguard their investments. This section delves into three critical components of wallet security: private key generation methods, multi-signature configurations, and encryption standards.
Private Key Generation Methods
The foundation of a bitcoin wallet's security lies in its private keys, which grant access to the user's funds and authorize transactions. Private key generation methods are crucial in ensuring that these keys are created securely and are resistant to unauthorized access.One common method is the use of random number generators (RNGs), which produce cryptographically secure random numbers to create private keys.
These RNGs must be robust to prevent predictability, as any weakness could allow attackers to guess or brute-force the keys. Additionally, many wallets implement Hierarchical Deterministic (HD) key generation, which creates a tree-like structure of keys from a single seed phrase. This method not only enhances security but also simplifies backup and recovery processes, as users only need to remember one seed phrase to regenerate all associated keys.
Furthermore, advanced wallets may utilize hardware security modules (HSMs) for key generation. HSMs are specialized devices designed to generate and store cryptographic keys securely, ensuring that private keys never leave the device and minimizing exposure to potential threats.
Multi-Signature Configurations
Multi-signature (multisig) configurations add an extra layer of security by requiring multiple private keys to authorize a transaction. This approach significantly reduces the risk of theft since a single compromised key is insufficient for unauthorized access. In a typical multisig setup, a wallet might require signatures from two or more different private keys before executing a transaction.
This method is particularly beneficial for organizations or individuals managing substantial amounts of cryptocurrency. By distributing key management responsibilities among multiple parties, multisig wallets enhance security and accountability. For instance, in a three-of-five multisig configuration, any three out of five designated signers must approve a transaction before it can be executed. This ensures that even if one or two keys are compromised, the funds remain secure.
Additionally, multisig configurations can facilitate collaborative management of funds, making them ideal for joint accounts or shared business ventures. This collective approach not only bolsters security but also fosters transparency among participants.

Encryption Standards Comparison
Encryption plays a vital role in protecting sensitive data within bitcoin wallets. Various encryption standards are employed to secure private keys and transaction information from unauthorized access. One widely used standard is AES-256 (Advanced Encryption Standard with a 256-bit key), known for its robustness and efficiency in encrypting data.
AES-256 ensures that even if an attacker gains access to the storage where private keys are kept, they cannot use those keys without decrypting them first—an operation that is computationally infeasible without the correct encryption key. Many reputable wallets implement AES-256 encryption to safeguard user data effectively.Another important aspect of encryption is ensuring secure communication between the wallet and external servers.
Protocols like TLS (Transport Layer Security) are essential for encrypting data in transit, preventing interception and man-in-the-middle attacks during transactions. By using TLS, wallets ensure that sensitive information remains confidential and unaltered as it travels across networks.
How Transactions Works
Understanding the mechanics behind Bitcoin transactions is essential for anyone looking to engage with this cryptocurrency effectively. At its core, a Bitcoin transaction represents the transfer of value from one address to another, facilitated by a decentralized network of nodes. This process involves several key steps, including transaction creation, broadcasting, and verification.
Transaction Creation
The journey of a Bitcoin transaction begins when a user decides to send Bitcoin to another party. This process requires the sender to access their wallet application, where they will input the recipient's Bitcoin address and the amount they wish to send. The wallet then constructs the transaction, which consists of two main components: inputs and outputs.
Inputs refer to the Unspent Transaction Outputs (UTXOs) that the sender wishes to spend. Each UTXO represents a previous transaction in which the sender received Bitcoin but has not yet spent. To illustrate, if Alice wants to send 0.5 BTC to Bob and she has previously received 1 BTC in a single UTXO, her wallet will use this entire UTXO as an input for the new transaction.
Outputs are where the funds are directed. In Alice's case, one output will send 0.5 BTC to Bob's address, while the remaining 0.5 BTC (the "change") will be sent back to Alice's wallet in a new UTXO. This mechanism ensures that all inputs are fully utilized, as Bitcoin transactions cannot send partial amounts from a single UTXO without using it entirely.
Broadcasting the Transaction
Once the transaction is created and signed using Alice's private key—an essential step that authenticates her ownership of the funds—the wallet broadcasts this information to the Bitcoin network. The broadcasted transaction is picked up by nodes throughout the network, which independently verify its validity based on predefined rules.
This verification process includes checking that Alice has sufficient balance (i.e., that her inputs are valid UTXOs), ensuring that the digital signature is correct, and confirming that the transaction adheres to network protocols. If a node deems the transaction valid, it propagates it further across the network until it reaches miners.
Mining and Confirmation
Miners play a crucial role in finalizing transactions. They collect valid transactions from a waiting area known as the mempool and bundle them into blocks. Each block has a limited size, so miners prioritize transactions based on factors such as transaction fees—higher fees typically result in quicker inclusion in a block.
Once a miner successfully solves a cryptographic puzzle (a process known as proof-of-work), they add their block to the blockchain, which is a public ledger of all Bitcoin transactions. At this point, Alice's transaction receives its first confirmation. As new blocks are added to the blockchain—typically every ten minutes—her transaction gains additional confirmations. A common practice is to consider a transaction finalized after it has received six confirmations, which usually takes about 30-60 minutes.
Finalization and Irreversibility
Once confirmed, Bitcoin transactions become irreversible; they cannot be altered or undone. This characteristic emphasizes the importance of double-checking recipient addresses and amounts before sending funds. The security provided by bitcoin ensures that once a transaction is recorded on the timechain, it remains there permanently and transparently accessible to all network participants.
Basically, sending and receiving Bitcoin involves creating a transaction with inputs and outputs, broadcasting it for verification by nodes, and ultimately having it confirmed by miners on the timechain. Understanding these mechanics not only enhances user confidence but also helps the users have a responsible cryptocurrency management practices.
Fee Management Strategies
Understanding Bitcoin transaction fees can be a difficult task, especially during periods of high network congestion. However, employing strategic fee management techniques can help users minimize costs while ensuring quick transaction confirmations. This section shows effective strategies for optimizing Bitcoin fees, focusing on timing, UTXO management, and other tricks.
Timing Transactions for Cost Efficiency
One of the simplest yet most effective strategies for reducing transaction fees is to time transactions during periods of low network activity. Bitcoin transaction fees operate on a free-market principle, where users can set their fees based on current demand. During peak times, when many users are trying to send transactions simultaneously, fees can skyrocket.
Conversely, during off-peak hours, fees tend to be significantly lower.To optimize fee management, users can monitor network conditions using tools like mempool.space, which provides real-time data on current fee rates and congestion levels. By scheduling transactions when demand is low, users can take advantage of reduced fees while ensuring their transactions are processed efficiently.
Efficient UTXO Management
Another critical aspect of fee management involves understanding and managing Unspent Transaction Outputs (UTXOs). UTXOs represent the available balance in a Bitcoin wallet and play a crucial role in transaction creation.
By consolidating smaller UTXOs into larger ones, users can reduce the overall number of inputs required for future transactions. This consolidation minimizes fees since Bitcoin transaction costs are often determined by the size of the transaction in bytes rather than the amount being sent.
For example, if a user frequently receives small amounts of Bitcoin, they may end up with numerous tiny UTXOs. When it comes time to send a transaction, using multiple small inputs can lead to higher fees due to increased data size. By periodically consolidating these small UTXOs into a single larger output during times of low network activity, users can streamline future transactions and reduce associated costs.
Leveraging Advanced Technologies
Technologies like the Bitcoin Lightning Network offers innovative solutions for reducing transaction fees. The Lightning Network operates as a second layer on top of the Bitcoin blockchain, allowing users to conduct off-chain transactions through payment channels. This method significantly decreases congestion on the main blockchain and results in much lower fees for smaller or frequent payments.
Using the Lightning Network not only reduces transaction costs but also enhances transaction speed—payments are nearly instantaneous since they do not require confirmation from miners. For businesses and individuals who frequently send small amounts of Bitcoin, integrating Lightning Network capabilities into their wallets or payment systems can lead to substantial savings over time.
Using Segregated Witness (SegWit)
Another effective strategy for managing Bitcoin transaction fees is to utilize wallets that support Segregated Witness (SegWit) technology. SegWit reduces the size of data packets by separating signature data from transaction data. This smaller footprint means that SegWit transactions typically incur lower fees compared to traditional transactions.
By adopting SegWit-compatible wallets and ensuring that transactions are processed using this technology, users can benefit from reduced fees while also contributing to overall network efficiency. Many modern wallets now offer SegWit support as standard functionality.

Mastering Bitcoin transaction fees requires a proactive approach that combines strategic timing, efficient UTXO management, and leveraging advanced technologies like the Lightning Network and SegWit.
By staying informed about network conditions and employing these techniques, users can minimize their transaction costs while enjoying the benefits of Bitcoin's decentralized financial system.
Backup Systems and Recovery Protocols
In the bitcoin industry, keeping your seed phrase secure is paramount for safeguarding your digital assets. A seed phrase, often a sequence of 12 to 24 words, serves as the master key to access your wallet and recover funds in case of device loss or failure. This section explores effective backup systems and recovery protocols, emphasizing the importance of physical security and innovative storage solutions like Stamp Seed and Cryptosteel Capsule.
Importance of Secure Backups
The primary goal of backing up a seed phrase is to ensure that it remains accessible only to you while being protected against various risks, including theft, fire, water damage, and natural decay. Traditional methods, such as writing the seed phrase on paper, can be vulnerable to physical deterioration or loss. Therefore, employing more durable solutions is crucial for long-term security.
Innovative Storage Solutions
Stamp Seed
The Stamp Seed method involves engraving your seed phrase onto a durable metal plate. This technique offers significant advantages over paper backups, as metal can withstand extreme conditions such as fire and water damage. By stamping the words into metal, users create a permanent record that is resistant to wear and tear. This method not only protects against environmental threats but also ensures that the seed phrase remains legible over time.The process typically involves using a stamping kit that allows users to imprint each word of their seed phrase onto a metal surface. The result is a robust backup solution that can be stored securely in a safe or safety deposit box. The durability of stamped metal makes it an excellent choice for those who want peace of mind regarding their cryptocurrency holdings.
Cryptosteel Capsule
Another innovative solution is the Cryptosteel Capsule, which offers a secure way to store seed phrases in a compact and resilient format. The Cryptosteel Capsule is made from stainless steel and designed to withstand extreme conditions, including fire, water exposure, and physical impact. Users can insert their seed phrases into the capsule using tiles that represent each word.This method provides several benefits:
- Durability: The stainless steel construction ensures that even in catastrophic events like house fires or floods, the seed phrase remains intact.
- Discreetness: The capsule can be stored inconspicuously, reducing the risk of theft.
- Ease of Use: The design allows for straightforward assembly and disassembly, making it user-friendly for individuals who may not be technically inclined.
Best Practices for Backup Storage
Regardless of the method chosen, there are several best practices to follow when backing up your seed phrase:
- Physical Security: Store your backup in a secure location, such as a fireproof and waterproof safe. Consider using multiple secure locations to mitigate risks further—one copy at home and another in a trusted bank's safety deposit box.
- Access Control: Ensure that only trusted individuals have access to your backup storage locations. Avoid hiding your backups in places where you might forget them.
- Regular Checks: Periodically inspect your backup solutions to ensure they remain intact and legible. This practice helps identify any potential issues before they become critical.
- Encryption: If you choose digital methods for storing your seed phrase (e.g., encrypted USB drives), ensure that strong encryption protocols are utilized to protect against unauthorized access.
Threat Landscape: Common Attack Vectors
The cryptocurrency ecosystem is rife with threats, as malicious actors continuously seek to exploit vulnerabilities for financial gain. Understanding these attack vectors is crucial for users and organizations to implement effective security measures. This section explores several prevalent attack methods, including exchange hacks, phishing attacks, social engineering tactics, and the emerging threat known as "Dark Skippy," along with the concept of the "$5 wrench" attack.
Exchange Hacks

One of the most significant threats in the cryptocurrency landscape is exchange hacks. Cryptocurrency exchanges are prime targets due to the large volumes of assets they hold. High-profile incidents, such as the Mt. Gox hack in 2014, which resulted in the loss of 850,000 BTC, highlight the vulnerabilities inherent in centralized exchanges. Attackers often exploit weaknesses in exchange security protocols or even use social engineering tactics to gain access to user accounts.

Phishing Attacks
Phishing remains one of the most pervasive and effective attack vectors targeting btc users. This method involves tricking individuals into revealing sensitive information, such as private keys or seed phrases, by posing as trusted entities. Attackers may create fraudulent websites or emails that mimic legitimate exchanges or wallet providers to steal user credentials.
In recent years, sophisticated phishing schemes have emerged that leverage social media platforms and fraudulent advertisements. For instance, attackers may create fake ads for popular wallets, directing users to counterfeit sites designed to harvest login credentials and private keys.
Social Engineering Attacks
Social engineering attacks exploit human psychology to manipulate individuals into divulging confidential information or performing actions that compromise their security. These attacks can take many forms, from impersonating technical support personnel to conducting elaborate pre-operational research on potential victims.
For example, North Korean state-sponsored actors have been known to conduct tailored social engineering campaigns against employees of Bitcoin and crypto-related businesses. By gathering information from social media profiles and professional networking sites, attackers can craft convincing messages that lead victims to unwittingly install malware or provide access to sensitive company data.
The psychological manipulation inherent in social engineering makes it particularly challenging to defend against through software solutions alone. Education and awareness are critical components of a comprehensive security strategy to help users recognize and avoid these types of attacks.
Dark Skippy: A New Threat Vector
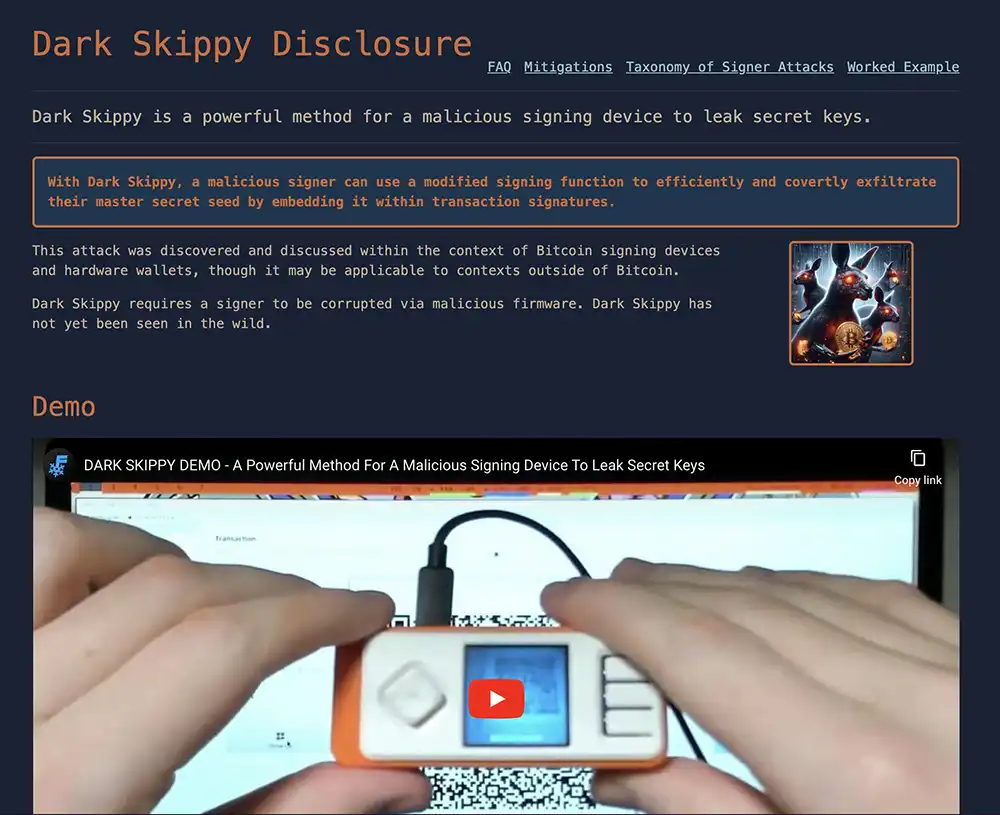
The "Dark Skippy" attack vector is a sophisticated method that allows a malicious signing device to covertly exfiltrate a user's master secret seed by embedding it within transaction signatures.
This attack exploits weaknesses in the signing process, specifically by manipulating the nonces (random numbers) used in Schnorr signatures. Unlike traditional attacks that require dozens of transactions to leak a secret seed, Dark Skippy can achieve this in just two signatures, making it a highly efficient and dangerous threat.
The $5 Wrench Attack

The "$5 wrench" attack is a metaphorical term that represents a physical threat where attackers resort to intimidation or violence to obtain access to a victim's cryptocurrency holdings. This type of attack emphasizes the importance of not only securing digital assets but also considering personal safety and physical security.
In a $5 wrench scenario, an attacker may confront a victim with a weapon or other forms of coercion, demanding access to their wallets or private keys. This highlights a critical aspect of bitcoin (and crypto in general) security: while digital defenses are essential, users must also be aware of their physical surroundings and take precautions against potential threats.
Wallet Selection Criteria Matrix
Choosing the right cryptocurrency wallet is a critical step in managing digital assets securely and efficiently. With a plethora of options available, it can be overwhelming to determine which wallet best suits your needs. This matrix outlines key criteria to consider when selecting a wallet, helping users make informed decisions based on their specific requirements.
| Criteria | Description |
|---|---|
| Purpose of Use | Determines whether the wallet is suited for daily transactions (hot wallets) or long-term storage (cold wallets). |
| Security Features | Includes 2FA, multi-signature support, and encryption to safeguard assets. Consider the wallet’s security track record. |
| Supported Cryptocurrencies | Some wallets support only Bitcoin, while others accommodate a wide range of altcoins and tokens. |
| Wallet’s Reputation & Reviews | Research user reviews, security history, and industry recognition to gauge trustworthiness. |
| User Interface & Functionality | The wallet should be intuitive and easy to navigate, especially for beginners. Look for accessible support resources. |
| Fees and Costs | Review transaction fees, withdrawal charges, and any hidden costs before committing to a wallet. |
| Backup & Recovery Options | Ensure the wallet offers a reliable backup mechanism, such as seed phrases or recovery keys, to prevent loss of funds. |
Purpose of Use
Understanding the primary purpose for which you need a wallet is essential. Are you looking for a wallet for everyday transactions, long-term storage, or perhaps for trading purposes? Hot wallets, which are connected to the internet, offer convenience for frequent transactions, while cold wallets provide enhanced security for long-term holdings. Clearly defining your goals will guide your selection process.
Security Features
Security should always be the top priority when choosing a bitcoin wallet. Look for wallets that offer robust security features such as:
- Multi-Signature Support: Requires multiple approvals to authorize transactions, making it harder for a single point of failure to compromise funds.
- Encryption: Protects sensitive data from unauthorized access.
- Air-Gapped Options: Reduces exposure to online threats by keeping private keys always offline.
- Self-Destruct Mechanisms: Some wallets erase stored data after multiple failed PIN attempts to prevent brute-force attacks.
Additionally, consider the wallet's track record regarding security incidents and how they were handled.
Supported Cryptocurrencies
When evaluating cryptocurrency wallets, the scope of supported assets can significantly impact both security and user experience. Wallets designed exclusively for Bitcoin often benefit from streamlined codebases, inherently minimizing potential vulnerabilities and attack surfaces—a critical advantage in safeguarding digital assets.
While multi-currency wallets may appear versatile for diversifying into altcoins or interacting with DeFi platforms, their expanded functionality introduces complexity, which can heighten security risks. Additionally, Bitcoin’s established credibility and decentralized design stand in stark contrast to the proliferation of alternative cryptocurrencies, many of which lack comparable transparency or serve as speculative assets with unproven—or even questionable—long-term value. Prioritizing wallets focused on Bitcoin aligns with a security-first approach while avoiding exposure to projects of dubious legitimacy.

Wallet’s Reputation and Reviews
Researching the reputation of the wallet provider can provide valuable insights into its reliability and security practices. Wallets with strong user bases and positive reviews are often more trustworthy, as they typically invest in robust security measures. Look for any awards or recognition within the bitcoin community, as these can indicate a commitment to quality and user safety.
User Interface and Functionality
A user-friendly interface is vital, especially for those new to cryptocurrency. The wallet should have an intuitive design that makes it easy to navigate features such as sending and receiving funds, managing assets, and accessing settings. Additionally, check if the wallet provides clear instructions and support resources to assist users in case of issues.
Fees and Costs
Understanding the fee structure associated with a wallet is essential for managing costs effectively. Some wallets charge transaction fees based on network conditions, while others may have fixed fees or subscription models. Be sure to review any hidden costs related to withdrawals or exchanges within the wallet.
Backup and Recovery Options
A reliable backup and recovery system is crucial for ensuring access to your funds in case of device loss or failure. Look for wallets that provide straightforward backup procedures, such as generating seed phrases or recovery keys. Ensure that you understand how to restore your wallet using these backups.
Advanced Features: Lightning Network Integration
The integration of the Lightning Network into Bitcoin wallets represents a significant advancement in the usability and functionality of cryptocurrency transactions. As a Layer-2 scaling solution, the Lightning Network addresses Bitcoin's inherent limitations regarding transaction speed and cost, enabling users to conduct fast and inexpensive transactions. This section explores the benefits of Lightning Network integration, its operational mechanics, and its implications for everyday Bitcoin usage.
Enhancing Transaction Speed and Cost Efficiency
One of the primary advantages of the Lightning Network is its ability to facilitate near-instantaneous transactions at a fraction of the cost compared to traditional on-chain transactions. By allowing users to create payment channels that enable off-chain transactions, the Lightning Network reduces congestion on the main Bitcoin blockchain. This capability is particularly beneficial during periods of high network activity when transaction fees can skyrocket.
For example, wallets like Breez and Coinos have integrated Lightning capabilities to enhance user experience. Breez, known for its non-custodial mobile wallet solution, allows users to send and receive payments instantly without compromising privacy or security. The integration with Coinos further exemplifies how Lightning can streamline Bitcoin transactions, making it practical for everyday use.
Operational Mechanics of the Lightning Network
To use the Lightning Network, users must first open payment channels with other participants. This process typically involves locking a portion of Bitcoin in a multi-signature address, which serves as collateral for future transactions. Once a channel is open, users can transact back and forth without needing to record each transaction on the blockchain until they choose to close the channel.This off-chain model significantly enhances scalability. Instead of processing each transaction individually on the blockchain, multiple transactions can occur within a single channel, only requiring an on-chain transaction when the channel is closed or settled. This reduces the overall load on the Bitcoin network while allowing for microtransactions that would be impractical with traditional fees.
Everyday Use Cases

The integration of the Lightning Network transforms how Bitcoin can be used in daily life. With wallets that support Lightning payments, users can make quick purchases at cafes, grocery stores, or online retailers without converting their Bitcoin into fiat currency. This seamless off-ramping capability allows individuals to leverage their digital assets in real-world scenarios effortlessly.
For example, wallets like Blink have made significant strides in simplifying Bitcoin interactions by incorporating Lightning Network features. Users can conduct small transactions quickly and efficiently, making Bitcoin as easy to use as swiping a card or using a mobile payment app.
Privacy and Security Considerations
While the Lightning Network offers numerous benefits, it also introduces new considerations regarding privacy and security. Transactions conducted via Lightning are not recorded on the blockchain until channels are closed, which can provide enhanced privacy for users. However, this also means that users must be diligent about managing their payment channels and ensuring they maintain sufficient liquidity for ongoing transactions.
Moreover, while non-custodial wallets like Breez allow users to retain control over their funds, custodial solutions may require trust in third-party providers to manage channels effectively. So, users should carefully evaluate their options based on their comfort level with these trade-offs.
Maintenance Checklist for Long-Term Hodlers
For long-term hodlers, maintaining the security and integrity of digital assets is crucial. A well-structured maintenance checklist can help ensure that your investments remain safe and accessible over time. This guide outlines essential practices for managing your cryptocurrency holdings effectively, focusing on security, record-keeping, and hardware upkeep.
Secure Storage Solutions
Use Hardware Wallets: For long-term storage, consider using a hardware wallet such as Trezor, Coldcard or other established companies. These devices store private keys offline, significantly reducing the risk of hacks or unauthorized access. Ensure that your hardware wallet is regularly updated with the latest firmware to protect against vulnerabilities.
Backup Recovery Phrases: Store your recovery phrase in a secure location, such as a safe or safety deposit box. Avoid digital storage methods unless encrypted, as this can expose you to risks if your devices are compromised.
Regular Software Updates
Keeping your wallet software up to date is essential for maintaining security. Regular updates often include patches for known vulnerabilities and enhancements that improve functionality. Set reminders to check for updates every few months or whenever you hear about significant security improvements in the cryptocurrency community.
Record-Keeping Practices
Test Your Wallet Backup and Functionality: When generating a new wallet, first back up the seed phrase on paper or metal.
Before using it for transactions, verify that your backup works correctly. A good routine is:
- Load your new wallet with a negligible amount.
- Send a small transaction to another wallet.
- Wipe the wallet (erase memory).
- Restore the wallet using your seed phrase.
- Send another transaction, ensuring it doesn’t use the full UTXO, so you can also check if change addresses function properly.
Maintain Detailed Records: Keep comprehensive records of all transactions, including dates, amounts, recipient addresses, and any associated fees. This information is vital for tax reporting and tracking your investment performance over time.
Export Transaction Histories: Regularly export your transaction history from exchanges and wallets to safeguard against potential data loss. Aim to do this at least every three months or before closing any accounts.
Security Protocols
Enable PIN: Wherever possible, enable the PIN on your wallets and exchange accounts to add an extra layer of security. This helps protect against unauthorized access even if someone gets his/her hands on your wallet.
Wary of Phishing Attempts: Stay vigilant against phishing scams that attempt to steal your credentials or private keys. Always verify URLs before entering sensitive information and avoid clicking on suspicious links in emails or messages.
Periodic Hardware Checks
If you use a hardware wallet, periodically inspect it for physical damage or wear. Ensure that all buttons and ports function correctly, and clean the device as necessary to prevent dust accumulation. Test also sending/receiving funds and confirm change addresses work to validate proper setup.
Diversification of Storage Locations
Consider diversifying where you store your cryptocurrency holdings. For example, you might keep a portion in a hardware wallet at home while storing another portion in a safety deposit box or with a trusted custodian. This strategy mitigates risks associated with theft or loss.
Assessing Investment Performance
Regularly review the performance of your bitcoin/cryptocurrency investments to ensure they align with your long-term financial goals. This assessment can help you make informed decisions about whether to hold, sell, or diversify further.
Bottom Line
Choosing the right Bitcoin wallet involves understanding your specific needs regarding security, convenience, and use case.
By familiarizing yourself with the types of wallets available and implementing robust security measures, you can effectively manage your Bitcoin holdings and safeguard your investments against potential threats. Whether you are a casual user or a long-term holder, taking these steps will enhance your experience in the cryptocurrency ecosystem.